Net Banking is quite common and an important banking feature in current days. Using net banking you can surely save lots of time by doing all those transactions from your computer which generally you can do by visiting bank. You can transfer money, pay bills, do online shopping, check balance and many more using the same. So there are lots of benefits of it. But still many people think that net banking is not safe and can harm your money via hacking and other related stuffs. True, it is not 100% safe but for which thing you get such full assurance. Yes it can be risky if you not follow some basic safety majors but if you follow them properly and follow all those steps which are important for keeping your account safe then you can use it without any problem. I am using net banking facility since 7 years, I have done many transactions using it like online shopping, money transfer, etc. and so far I have never faced any problem related to security. So it is good facility if we know how to use it properly. Let’s talk about all those concerned things which should be keep in mind if you are also using the net banking or thinking about to use the net banking.
Tips for using Net Banking
Choose a strong password: First thing is to set the password for your net banking account. Make sure that you are using strong enough password which cannot be predicted by anyone, even by your family members. It should be known only to you and should not be not easy like your birth date or mobile number which can be guessed by anyone. So make sure that you are using a strong enough password like mixing numbers with letters. Keeping password with only letters or only number is counted as easy password, so don’t do that and choose strong password but choose it properly so that you can remember it later on. Lol.
Never type password publicly: Publicly means whenever you login to your account make sure that you are not typing your password in front of any unknown person or person on whom you don’t trust more. Net banking is an important thing so that you should understand about its importance, you can’t just type password in front of anyone, that unknown person can check out your password and that can be problem for you later on. So make sure that you are typing it privately so that no one can see it.
Change your password regularly: This is also an important thing. You should keep changing your password regularly. So that even if someone knows it or hacks it, by changing it regularly you can keep your account safe from such attacks. You should fix a certain time interval for changing your password like once in a month, it is a good habit to keep your account safe and to keep your password safe from others.
Use more Authentication features: These days social sites and email sites are providing more authentication processes than just a password. For example, before logging in to your account they provide you some kind of pin to your registered mobile number, so after entering that pin only you can open your account. Now even banking sites are providing such higher protection authentication process for your net banking account. If you are having such features on your banking site then it is more preferable to use it too than only single password.
Never login from unknown or public computer: This is most important thing when you are using net banking for your bank account. You should only use your net banking account on your personal computer. I have seen that many people use net banking on cyber cafe in a hurry when they are outside and not having their computer with them. But let me tell you this is a bad habit and can be dangerous for your net banking account. Any public computer may have installed some malicious software on it which can hack your password in it; same thing goes for any unknown computer. That’s why I am saying that better to be safe and only use it on our personal computer. No matter what, it is better to avoid unknown computers and public computers for Net banking. You should make it a practice.
Never share your details: You should never share your net banking details or account related details with anyone. Not only offline but also online. I mean to say you may get many phishing mails for asking your net banking details. For example some fake banking mails may come to you for asking your password and some other personal details. Never share password or any personal detail to such mails without confirming about it with your bank. Banks never ask such details on email. So be aware of this thing and never share your personal details with any unknown person and also on online.
Use paid antivirus and keep your computer virus free: It is important to keep your computer clean from any kind of virus and spyware. Virus and other malicious things can certainly affect net banking process and it may lead to hack your account. So it is better to use best and licensed antivirus if you are depend on net banking facility more. You can even use free antivirus but paid thing will serve you more and give you more security obviously. Other thing is always keep updated antivirus. These days new and new virus found by hackers, so better we update our antivirus regularly to stay safe from them.
Don’t forget to logout from your account: I have seen many people that don’t use to logout their different accounts like from social sites or email account. Let me tell you net banking is not like checking social sites and emails, it is very important thing in compare to them. You should always logout your account immediately after you complete your work on it. Without logout it may raise problems to you. So never forget to logout from your net banking account after you complete your work with it.
Open bank site by Bank site URL: Many people use search engine to open links and different sites. But better you not follow the same for net banking site. It is better you directly write your net banking site URL on browser and open it directly. You should also not use email links which redirects you to your net banking site. This may not sound more risky to you but sometime it can be very risky to you if you by chance redirected to wrong and fake site of your banking site. So be careful with it.
Stay alert from Phishing mails: I have already told you about it. You may get many phishing mails which will ask you about banking details and net banking password to complete some kind of tasks. Never fall for this thing. Even you get mail which is very similar to bank mail I will advise you to not to open any kind of link from mail. You can check things directly from your banking site by typing its URL directly into your browser. Some phishing mails may come with your bank name and it look exactly same as your banking mails, but never fall for it and give any kind of personal details. I already told you that mostly bank not ask any kind of personal details and passwords via mail.
Online shopping via net banking: If you are doing any kind of online shopping using your net banking account. Then better you go for genuine online shopping sites which are old and reliable. You should never use your net banking account with any new or unknown site which may lead to you with some kind of problem later on. They can hack your account with given details and then just disappear from the online world. So better you do all necessary investigation about the site with which you are using your net banking account.
Keep checking your account: Even if you are following all the safety majors you should check your account activity regularly. It is not necessary but it is a good habit. By this way you can make sure about all transactions done by you with your account. So you can also track any improper activity going on with your account by this way. So just decide regular interval of time for checking your account activity and keep doing it on regular base.
So this is it. I have mentioned about all the points which I came to know about with my experience so far with net banking. I am sure this will be helpful to those who want to start with the net banking feature and worried about security related to it. Just follow them properly and keep checking your net banking account activity on regular basis, I am sure you will be safe without any problem. So be safe and have fun.
Introduction:
Modern day businesses work on more than one factor. Due to scope and perimeter of business, many units of it stay far and wide at different destinations. Coordination among all these subunits are important. Communication among different parts of the organization creates a sense of integration within administrative units. It leads to speedy decision making and correct execution of orders on separate legs of the organization. Proper communication network from within different legs of organization makes coordination and proper implementation of different ideas. With the advent of a new Information Technology (IT) initiative, there are plenty of applications and devices that can virtually function with customers at different interactive forums. Information technology network is a vehicle of communication medium with fully automation facilities for clients to take advantage of early information releases. Conversely, the same IT network collects real-time analytics of visitors’ advent to the server and provides opportunities for administrators to analyze trends and demand of customers.
It helps smooth transitions of real time customer relationship management (CRM) with immediate consumers. It serves to decrease delaying time and increase efficiency by creating a constant channel of communication between industries and suppliers. The dashboard of IT and the process of CRM help management to create proper business objectives to reach decisions about the business. It helps to support new business models suitable for rapid growth of business by implementing suitable adaptations techniques from CRM’s analytics, insights and sensors. All these create a network integration services (NIS) which are best to suit any type of network at different responsive zones from situation airing out of different business consequences. NIS prepares Organization for upcoming dynamic challenges reaching out from different environments as consequences of complete change of market dynamics and competitors advantages. NIS has every solution for organizations in times of emergency and this sets it as the most preferable and dynamic platform for business ventures to adapt different challenging situations with a strong shelf enabled tool to compete with any situations.
Challengers to market leaders:
Business is not constant. If there is a monopoly of any company at some point in time in a particular place, at some other time there will be many competitors who enter to topple the market leader. Market leaders should be empowered to attack and defend from such business rivals so as to stay at the top at any eventualities. Almost all the time, business needs are constantly challenged with emerging technologies to wipe those business organizations within the shortest possible of time. Here, is a case in a failed example where a market leader comes to grassroots within shortest possible of time. Bajaj brought out scooter and it became a huge success. Distribution of scooters was not good as it failed to create a complete hub and spoke in logistic management all around India. Demands for such scooters are on higher side due to price affordability and conveniences for middle income groups to have a two wheeler in their perusal. People had to wait here for more than a year to receive their scooter. Their hard-earned money is booked and it stays with the company for more than a year. Many parents used to look scooter prior to one year of their daughter’s marriage and had been waiting for long to receive such. In the mean time, one hardware subsidiary of this company parted ways and it became a single company and an immediate challenger to Bajaj scooters. Slowly, Vespa the immediate challenger became number one and the market leader slipped into second place. Vespa introduced immediate supply of scooters and for the first time it introduced showroom for two wheeler in many capital cities all across India. Instead of there waiting for months, people went to other companies that provided good products. Due to lack of changing insight of Bajaj in realizing the changing demand and perception of customers, it failed to stay at the top position for the remaining time.
In the coming years, Honda Company introduced motor cycles which were slightly lighter in nature than a bullet from Enfield and Rajdoot. They became hugely popular but instead of grabbing market share of Enfield it cut across the market share of scooters. In this way, many upcoming challengers to Bajaj scooters such as Vespa and Bajaj itself had to completely shut down their scooter businesses. These companies had seen such humongous failure due to vendor-neutrality and lack of consultative form of decision making at the highest strata of enterprise resource planning (ERP). These stayed with network delivery systems to immensely coordinate in attending different business goals in different challenging circumstances. Business models are created to prepare the organization to create a field suitable to revert back different business challenges at different point of times. Business challenges are used by clients to create a sense of familiarity while browsing for different information technology enabled service (ITeS). Increase use of cloud-enabled services (CES), mobile enabled services and applications (MESA), build your own device (BYOD) have empowered organizations to analyze real-time data analytics to optimize business performance that are dependable upon new and different blend of expertise of professionals contributing to the success of organization. While making research to buy a decent hosting for website, the author has to analyze different factors in his decision making processes. There are many web registrars who are offering expert website and domain hosting. Out of all these short-listed companies, prominence in reaching absolute decision comes from design of hosting website in reaching different settings easily with CRM. CRM is an essential and integral part of an emerging organization. It helps customers to decide and reach the conclusion and it gives them a comfort to upcoming company which they are going to work for now. All these parameters of attributes leads to single window decision making customers and it gives them fully optimized solution to reach sufficient conclusion to decide upon which host they want to work with.
Information technology enabled services:
For hosting registrar companies, round the clock assistance and guidance for customers is a genuine boon for spreading word-of-mouth from different areas all across the world. Web Registrar companies have customers from different zones of the world. A US (United States) Company might have customers from India, Brazil, South Africa and France. Time-zone all across these continents are completely atypical. For this round, the clock online and offline CRM can boost and optimize potential for growth of such companies. Due to spread of internet and business emergence among neo-middle classes all across society gives way for creation of their virtual presence with the help of website. It establishes the need for round-the clock access to application and data from different time-zones of the world. To web-hosting some third party applications such as ‘akismet’, ‘drop box’. Both these scripts can be automated with third party installed like ‘softaculous’ to create a complete automated install of self-hosted-website. This is an example, of how a good CRM coupled with a strong IT infrastructure in ITES can enhance perspective of business growth and optimize different solutions to bring forward source of competitive capabilities to float ahead among equals in the same marketing segment in business environment. All these critical issues if not cleared on time can have potential to harm business benefits.
These issues imply to all other distinct market dynamics. One hour of downtime of electronic commerce (e-commerce) website can inflict heavy loss of flow of revenue streams from internet enabled services, automated supply chains and inflict long-term damage to client relationships. It brings a bad name to the registrar and through word of mouth it spreads to different web masters leading to mass exodus of web hosting to different other web –registrars. Here, example comes from hosting registrars but it can be applicable to all segments of companies which are dealing with clients and fully dependable on the extreme satisfaction of customers. A bad name for companies from different hosting parameters can decrease considerably the productivity of its in-house employees and can decrease in-house expertise of these companies to a bare minimum level so as to create a sense of negative discourse from within different segment of the organization. All these organizations need a complete structured delivery methods depending upon complete overhaul of integrated solutions to create an immediate response time of server from any point of time after receiving a query. A practical road map for every organization is most which include future perspectives regarding goals and aims of organizations which can be clearly mentioned in each chapter and documents of the organization. Every employee must have recourse to such charters and must depend upon different online and offline aids to increase efficiency and functionalities in achieving set goals from within the boundaries of an organization. Sophisticated tools which determine different cost-effective and excellent ways to analyze growth of an organization can be accessed from different information technology enabled services at different point of time.
Common core state standardized requirements:
Business organizations have academic, technology, management benefits while constituting an integrated road map for digitally-driven customized marketing solutions. Every year, available technologies for corporate are spiraling into distinctive units, posing serious challenges to administrators of industries to create dynamic strategies to suit business organizations from time to time. With each new advancement and up gradation comes a fresh challenge for companies to make innovation and empowerment to face higher competitive environments. Fortunately, smart strategies for digital practices are becoming clearer. Business organizations are increasingly going for smarter integrated technologies which are cost-effective solutions for proper time-management of distributing unique information technology enabled services (ITES). Each organization has unique needs of demanding and requires different alternative strategies to suit local controls in practicing better digitally management solutions for immediate and prospective customers. Each organization has common core state standardized requirements (CCSS) to increase market participation and augment intrinsic talents of in-house staffs. CCSS recognizes first the inherent demand from within its employees and try to grab analytics of customer’s demand and choice of products and create customized units for different individual customer’s customized solutions to suit their marketing needs and basic demands.
CCSS creates a whole set of unique concepts for organizations to put forward different dynamic set up which are not available to other competitive organization in the same marketing segment. The inherently complex wish of the customer is measured through deep penetrative market permutations from different statistical methods to arrive at perfect elements to counter the competitor’s product and create a perfect niche product to remove immediate customers and build a unique market for a different set of products. CCSS not only serves customers better but also increase the effectiveness of organizations to accommodate modern economic realities Big well-known companies falling upon hard times are not uncommon. Taking the leaf out of Motorola mobile company, who has pioneered mobile services and push notifications which are being used by different companies, is now falling behind every mobile manufacturing vendors. Push notifications invented by Motorola is a futuristic technology and it is used by Android in giving virtual shortcuts to all internet synchronization features, is completely wasted by Motorola due to lack of futuristic vision in creating core state standardize requirements (CCSS) which should have been prime focus of this mobile driven hardware manufacturing-company.
Loss of trade secrets can impact negative growth for company:
When, resources go digital even while facing ongoing challenges such as financial, regulatory prohibitions, still many industries go for complete automation of the existing network in order to create a smarter world full of information where time matters the most. The answer to this is that technology prepares ground for new exciting ways to prepare the organization for the latest developments and trends. There are numerous research papers which have wholeheartedly discussed about impact of technology on industrial output and productivity. Most researchers have wholeheartedly agreed about, efficacy of implementation of a network server in driving out wide scale benefits to final output of the organization. Technology brings rapid change to basic functioning of an organization. It minimizes workforce response time, invigilates simulated work conditions and guard organization from further external attacks. Technology successes are not guaranteed at the ground level. It depends upon skills of the task force who confronts with those at the front-end level. In the long run, after super success of implementation of network tools which is available at different front-end office optimization scenario is slowly moving towards the trend of mobile and smart phone arena to enable the concept of bring your own device (BYOD) to the doorsteps of organizations. Historically, servers, databases and applications are important destinations for cyber attacks. More than 90 percentages of cyber attacks and out surge eminent from different weird zones.
Tiny credit card readers and small cameras can track credit card details and can telecast details through small GSM antennas. In this approach, many such credit and bank ATM frauds surfaced. There are many instances of fault of technology or faults arising out of smart implementation of technology lead to negative impacts on technology processing which ultimately create huge losses for individuals and companies. Loss of trade secrets can impact negative growth for the company. With the advent of Android and Apple mobile operating system, more and more losses of trade secret and moving of important files and information to hackers who bargain to immediate competitors of the corporation to sell classified documents. With smart features, most of smart phones have credit card readers, inbuilt camera for hidden capture of security details of credit card which leads to significant loss of revenues for individuals as well as for corporates. ATM card transactions, petrol pump card are also vulnerable to hack into security details which can open the floodgates access its credentials without administrator rights. There is a need for networking of all smart phones in use by corporate employee at corporate place so as to keep a vigilant eye on workers who are dealing with matter of extreme secrecy. If no such principles are there, then in no way, employees could be prohibited to take a snap shot of classified documents with smart phone and release elsewhere. Modern smart phones have a high intensity camera which can take high definition screenshot and then can send it elsewhere through different networking means. Think of a situation where companies have restricted access of USB (Universal serial bus) drive into the organization. Despite all these employees can take a screenshot and take away information about organizations in one go.
Layered firewall security:
Photographing of data on the screen cannot be stopped and cannot be banned altogether if mobiles are allowed within the premises of the organization. There are numerous examples of data breaching due to outdated flash content embedded within excel documents. Outdated Adobe, Flash and Microsoft Office products lead to a mass exodus of hacking elements reaching into the setting of data server and pinging back documents back to host of attacker’s computer. There is less evidence of mobile devices as an initial point of data entry, but certainly it creates suitable and congenial elements for hackers to find the secret path of entry into data-mining of organization. Surprisingly, most hackers and attackers have not yet been realized the potential of entry through smart phones for creating a data breach. There are a few issues that have been stopping most attackers to go through mobile devices.
Close end security system and single window security system:
Google concentrates on protecting data itself no matter which devices accesses it from which locations. This simplifies the process of security and gives a free hand to its employees to innovate and discover many new inventions that have been rolling in the arena of the world from time to time. Unlike many other enterprises which mostly concentrate on securing behavioral aspects of employees in keeping them out from any such security functionalities which the other side is completely restricting access to employees. It has various negative connotations as it completely restricts potentiality of employees to go for any such product innovation and research due to implementation of close-end security system. In the future, enterprises will need to make such amends and need to look beyond the perimeter of an organization to start again for building completely secure infrastructure of data warehousing It creates one point security system without bothering anything about the presence of different dynamics for infrastructure for safeguarding entire security terminal of organization. World is moving at a faster speed and in every minute unbelievable form of data are processed within the realm of organizations.
With the advent of smartphone and mobile phones, the role of cloud computing has entirely different connotations and this lead to the creation of light years of fast processing of data within coming two years. In the coming years whole set up of organizational attacks will be made in the perimeter of data security and for this enterprises need to recognize this and should treat all these imminent dangers in the manner they treat aliens in space. Space is a broad stretch of unimaginable land where the more you enter the more you lost. Similarly, the constitution of data inside servers is transcending all barriers of entry. The world of attackers is a completely different world constituting of blind folded fight between attackers and security administrators. There is little doubt that organizations are slowly moving towards completely mobility. Many enterprises are heavily dependent on ambulatory services. Mobile networking within an enterprise server is getting prominent, but slowly they are exposing security gaps within organizational spheres. It is duty of the organization to create combinations of security networking tools that can certainly fill security vulnerabilities all across organizational spheres.
Information security of organizations paves the way for distributed security levels:
According to research analyses, half of mobile phone users in the United States (US) have smart phones. Smart phones have every tool that can be used for various hacking purposes. Laptops, tablets and smartphones have increasingly paved the way for build your own device (BYOD) phenomena which are increasingly eroding privacy of individuals and enterprises. Information superiority in organizations paves the way for disturbed security levels, in which smart phone users are increasingly getting the upper hand from security management that manages enterprise security. Due to superior level of security all across organizations, advent of mobile security is increasingly getting paranoid in detecting lapses due to the advent of always-on connectivity. Mobile enterprises are increasingly getting paranoid about the strength of security by adopting different level of sandboxing security and installing applications on sandbox security. Sandbox security runs as if it is running under Android user interface and it scans and detects for application vulnerabilities and viruses before it completely installs itself on the dashboard. Still, there is no way, third party applications can intrude into the mobile system as they are also installed in sandboxes environment. With the advent of all these classes of advance security system most of enterprise security systems are not able to go as equal in creating a level playing field for organization.
It creates a sense of information superiority due to the advent of sandboxing environment. In organization, it is very difficult to create one such alternative secure environment as there is huge technological development need to be done which has not surpassed the passage of excellent so far. It is always important to identify what needs to provide protection. According to survey, more than 40% of workers want to access data through mobile devices. There are many such reasons such as accessing speed of data base and portability are prime factors in determining huge use of corporate data to mobile devices. Many enterprise servers are now providing fast mobile access for networks and this makes huge use of enterprise servers in the mobile environment. Most of these mobile devices run with android and Apple mobile-operating system and researches have proven that all these devices are prone to malware attacks in most times. System administrators of enterprises can no way identify such BYOD devices and can stop or control advent of malwares from these devices into enterprise servers.
Why organizations are compelled to introduce restrictive policy guidelines:
IT (information technology) security professionals need to understand and check the scope of the environment they can control from within ambit of organizational security framework and then they can allow such devices to run within organizational perimeters. They should carefully observe the behavior of operating systems, applications, network use, files for threats and vulnerabilities. These are tools which give visibility to your organization through third party devices which have semi-administrator rights from within organizations given to employees. Many organizations are building their own customized application control systems which can only work within limited administrator rights and it can erase every session and data cookie in order to have complete control of logistic data. Many such applications are giving users to authenticate every time they log on to the administrative account and such applications runs as mini applications for the specified session when employees log into enterprise server from whatever application environment. Such enterprise specific applications are configured to run with specific environments which apply to specific security parameters attending to attribute to log into the server environment. In this way, most of application environments are controlled and come under direct security environments. With BYOD movement there is an abrupt increase of productivity, efficiency and connectivity for employees with customers but there are many downsides to it were within a drop of eyes most of the data within an enterprise server can be at risk of being of stolen completely. BYOD makes organizational framework smooth and functioning within an organizational framework becomes easier and this creates scope for more experimentation and innovative practices from within organizational premises. The fact is that the more easily organizational processes become the more difficult for information technology (IT) security professionals to secure entire organizational framework.
The fact is that the smart phone can do more than what a basic mobile phone is capable of, such as calling, internet browsing, installing applications, streaming of videos, downloading and so on. Most of these functions are established with the help of the Internet and various specific applications which accesses different private profiles embedded within smart phones. This makes specific vulnerabilities and can provide safe passage for attackers to use a smart phone as a tool to enter into enterprise security. Most of times due to policy restrictions of enterprises, most users are banned from certain websites which have possibilities of hacking scripts and prohibited from installing third party applications on their device without proper authentication from IT security professionals in organizations. Numerous organizations are promoting BYOD for their own conveniences, but in parallel they are forcibly applying policy restrictions on such devices. This raises questions over the concept of BYOD policies where it is estimated to create a spontaneous environment devoid any such restrictive policies. However, sadly due to extremely worsen security environments organizations are compelled to introduce such guidelines.
How benefits of organization vary with satisfaction index of internal staffs:
Bigger enterprises should learn from Google’s way of securing its databases which strictly based on server side coding irrespective of devices and platform it is connecting to. Recently, I have opportunity for conducting a complete research on BYOD with numerous organizations, who just wanted to know pros and cons of implementing BYOD within organization. My sample size is on the lower side and it is still in progress but the result is apparent. The organization which has unlimited and unrestricted BYOD for workers has more benefits in terms of productivity, connectivity and satisfaction of employees. On the other hand, those organizations that have implemented restrictive BYOD have performed worse than organizations without BYOD. This goes on showing how the benefits of organization vary with satisfaction indexes of internal staffs. With the advent of completely mobile computing, most of general purpose tasks of organizations are now completely depend upon devices of individual workers. What if at some point of time, such devices got stolen or broken due to complete negligence of individual or from sheer ignorance, then the company is about compensating the employee for the loss of prime device? As per research, many companies are not willing to pay back the price of mobility to workers. They have been giving the convenience of data packs and mobile talk time workers. But when these mobiles are either lost or stolen, in most cases, these costs go to have to bear by individuals. In this case, enterprises are ignoring the utter security lapse of loss of phone and if these phones recovered by attackers and rivals than the whole set up a network server will have critical security encroachments. There should be a proper policy for lost phone under BYOD in order to have proper remote control with these phone so that in the long run when the user lost the phones, companies can immediately erase data remotely so that person who have this phone will not be getting any information about company.
Beware of organizational data server:
What if, the worker has to contract list of his relatives, friends and families in a lost phone. Then, it is nothing to bargain it for slightly uncomfortable feelings. What if the workers are dealing with classified documents of the company and he is contracting clients who have requested enterprise to keep their name secret and all those in contracts present in the lost phone. This can pose serious encroachments to the privacy of individuals and the company can face many such legal challenges of revealing names of such clients which they are not supposed to do so. In this approach, naturally enterprises are responsible for any such miscarriage of privacy policy of organizations. For this, it is highly essential for enterprises to make a robust connectivity among different mobiles phones used for official purposes. There should be a compelling case for shared governmental power of mobiles. Enterprises should install some tracking software and can observe and investigate mobile device behavior of employees from a distance. When it seems the device is either lost or stolen, then, immediately information technology security experts of companies must intervene and delete data from inbuilt storage and from flash storage of stylish phones. Time to time system administrators must look and scan BYOD mobile devices, whether they are storing any such email attachments or documents related to companies within the premises of smart phone device storage. With an updated Gmail interface of Android, most of these attachments are now automatically stored with goggle drive application of the same account. In this approach, when the thieves got hold of phones and could not find any information there, and can easily log in to goggle drive application to download automatically scanned documents. It is important in order to use such email applications which do not have any such automatic downloading of attachment to cloud server characteristics. BYOD is a complex process, but it is a very simple tool for attackers to infringe into such devices and play havoc with the data management server of the company.
Sandboxing security environment:
What if the user has credit card detail in his mobile devices and most of data about its security in there and when it comes in hand of attackers then a whole set up of credit ransom in account of such organization could play havoc financially to individuals as well as to organization. The principal point of action is regardless of whatever information comes to your phone from the organization. You are required to protect this and all singular should be super conscious about keeping mobile device safe. Depending on recent survey, most of BYOD devices are from Apple or from Google. Owing to constant innovation and challenges, most of these devices are now tangled with android mobile operating systems. There are some security challenges which pose grave security introspection while using Android enabled devices. Most of the top enterprises are now opting for cloud hosting environment and want their employees to work within sandboxing environment just like Android powered devices. With the advent of android most of BYOD networking have been completely secured with its sandboxing environments. It makes every application to use shared memory and runs within sandboxing environment and it enables the user to have responsibility of allowing access to different application on different settings of android dashboard. Android gives immense power to users.
It opens up the system and wants the user to decide the fate of the device. Here, the role of information security experts in organizations comes to the forefront and they can take over administrative rights of android and create a shared environment which will run within the perimeter of sandboxing elements. Entire BYOD network will be secure and safe from prying eyes of the attackers. Android users have to know it clearly whether he has to approve or deny permission to specify applications. Most users do not read nor concern about such rights while installing applications. Some good mobile antivirus companies have developed installation dashboard and it is advisable for users to employ such dashboard while installation of applications so that the third party installer will check everything on that application before fully administrator control is being given to specific applications. On the other hand, with Windows Mobile from Microsoft and Apple’s mobile operating system the entire security structure is being carried out by respective mobile companies and they have made extreme convenience for users to focus more on mobile computing and less on managing security setting of devices.
Go for genuine cloud back up:
Beware of services that cost you money. There are some applications such as dialing or texting application which may be more convenient for you to use it but on the other hand it can automatically send text messages to anyone without the user’s knowledge. This can be fully automated with file attachments are sent to the remote server without user’s knowledge. It is wise to delete such application as they are completely missing administrative rights given to such applications. Storage applications such as Dropbox, Google drive will need ability to read write and delete information and before installation it will ask you for such permission. Most users without reading permits such applications for such administrative rights. These storage applications can directly synchronized multimedia contents to cloud services and perform multiple backups when data connection is switched on. The reason behind this it says that there is no uniqueness in this application. Samsung offers 50GB of Dropbox storage to Galaxy users and in addition to this it offers 35 GB of cloud storage through Samsung Link. Drop box automatically uploads pictures took the camera to dropbox account and then in reverse show those pictures by phone even if those pictures are deleted from device storage places. Similarly, Google is offering 25GB for Google drive, which is a cloud hosting for files and multimedia contents and it also works like Drop Box within smartphone
Beware of stalkers and hackers:
Employees’ personal information in BYOD (build your own device) set up stays at phone book and calendars. Phone book consists of detailed information of individuals and clients with their email, website and screenshots. When mobile is stolen or theft, then this information could lead to severe privacy breach of clients who have requested to keep their identity secret while dealing with enterprises. Similarly, calendar creates a set up of schedules and meetings to be held and completed and if these information reaches to the hand of immediate competitors of organizations, then it could spell and impact deeply over routine decision making policies of enterprises. When, enterprises though of creating a secure environment for its employees, one should always be clear that security does not always comes from outside, but most of times, carelessness from among different segment of employees makes the organization the most vulnerable and creates huge financial loss. There are some widgets and applications which could access phone book and calendar events and for this it is essential for an organization to remain vigilant and examine that other applications users have installed on the phone. Through these applications hackers can steal sensitive and vital information and this can spell to be most destructive for data security of an organization. If you have stored various appointments of yours inside phone and these appointment details have taken by hackers than they can sell these data to competitors of your enterprise and in return they will get handsome money.
Competitors will reach to your clients prior to you and then they will take back the projects which have been with your organizations. All these have very damaging effects on organizational security as well as on it can implicit deep financial damage to organizations. There are some phone widgets and applications which have ability to read phone identity and state. Some application uses strictly private revelation in order to implement two factor authorization processes. This third party authorization can lead to severe damage of privacy of data and this links to revelation of classified documents of organizations to broadcast. These widgets can detect when you are on the phone and what you are talking about and to whom you are talking and it can record the entire conversation and can send to attackers through GPS transmission or using your own data connectivity. If you have GPS navigation enabled on your phone, they probably will find out exact locations of yours and where you have been and the time of stay on that location. All these prove to be most hazardous and dangerous for security of people as well as data security of organizations. From this information, a criminal would know when to break up into your house and stalkers would know the habit of your web browsing and exact times when you are privileged enterprises. All these can prove costly to security of data and processing of information. If not, stalkers would like to send malwares through your device in order to make the entire enterprise server slow unusable.
Secure all hands free device gateways:
With the advent of modern internet and high speed broadband connectivity most of internet connections are now fast and for this Wi Fi and Bluetooth tethering are possible within different devices. There are many video applications which can run through bluetooth transfer of videos. With the development of Bluetooth technology, videos and audios can be transmitted from one device to further through implementation of hands free devices gateways. Beware of such applications and it is not advisable to install those on official mobile devices. These applications can automatically send big video presentations from your phone to stalkers while internet is switched on and in this way. Most vital strategies of enterprise are revealed before all. There are some web browsers which are offering compressions of data for free and this requires severe intrusion into privacy of individual in order to know the exact location and internet protocol (IP) address of individual so as to redirect those data to their server and then redirect to phone users. It is alright when default web browser of android such as Chrome from Google do this as Google has always been good at securing privacy of individuals but on the other hand we have seen how other browsers such as Opera which is offering off road mode to users in order to compress data can intrude privacy and stalkers can have the option of using these short of route to regenerate entire device memory and take back all those to his own server.
A simple mistake of compressing the Internet in order to reduce high data transfer charges can place users to severe critical intrusion of privacy which never ever thought before. That is why advocates of free networking facilities to users in order to create a congenial environment in the work atmosphere are always right but what about associated problems that come from either ignorance or deliberate ignorance of users in creating a damaging security situations of enterprise servers. Always take care and think twice before permitting the application to storages and personal information. If an application like to access storage and personal information then carefully read its privacy policy and double check the name and reputation of the vendor from a through Google check in order to find details of information about the application vendor. It is wise to go for Yahoo questions and Quora search which have a very dedicated group of volunteers to work day in and out in order to give you a perfect lead and experience about such vendors.
Conclusion:
There are many widgets and applications that can help you to send messages in an easier way than default message application of android or some other mobile operating system devices. It can read, write and send messages to a different server without your knowledge by automatically switching on internet connectivity and send these messages to a remote server of stalkers. Beware of such hidden practices as some messages can be from your boss and can be of some serious secret information about your enterprise. There are some applications which can switch on the torch light within android device easily. Users should understand these features are automatically there inside deep default gadget setting of android and for this it is essential for every user to first look for default applications which are safer to use and can be brilliantly managed by information security officials of enterprises. A social engineering widget has the ability to detect the location and critical information from user’s account which has the requisite permission for user account control. In this way, even if BYOD has the responsibility of the employee but the perimeter of damage could include organizational data server. It is high time organizations should go for a thorough and proper creation of security policies for such devices. There are plenty of other security breaches, but these are some which I find extremely critical to work it out.
In this article, there are examples of how security can be breached through the simple process of ignorance by employees and there are certain loopholes of security which needs to be patched through significant behavioral changes through proper implementation of stricter policy controls all around perimeters of organization. Ultimately, you are the user which performs serious sanity checks of allowing administrative privileges to applications and gadgets. In both cases of enterprise scenarios as well as individual scenario of using smart phones, protecting privacy is single most important factor which needs to be respected and all these are in the hands of individuals who should be looking seriously privacy policies of applications before granting them administrative rights to run. There are some screen savers for smart phones and high end devices which want access rights to storages, personal information and internet access. For a screen saver, all these access rights have no meaning at all except collecting anonymous data and sending back to originating server. All these trivial matters need to be examined by persons before granting access rights. Before installation, think about function of widgets, installation details, access request permission and Google it to get proper feedback from other users. Solid network policies are foundations of good cyber security. Follow these guidelines carefully and obeys its restrictions to enjoy complete security. In this approach mobile, networks work nicely for businesses.
Facebook came into existence in March 2004 and has become globally popular today. This site is developed by Mark Zukerberg, a Harvard university student along with his friends. Initially access to this site was limited for the students of Harvard university and was later made open for the students of other colleges and universities. Soon the site became very popular among the students. The rising popularity immediately made the site open for teenagers of above 13 years and gradually Facebook won the heart of the people all over the world.
The founder and owner of Facebook, Mark Zukerberg is only 28 years old. He was born on 14 May 1984. His complete name is Mark Elliot Zukerberg. His father is a dentist and mother is a psychiatrist. Mark began to develop interest in programming from the age of 12 years. Seeing the interest of Mark in computers , his father appointed a private tutor for him. As a kid, Mark has developed many computer games just for the sake of fun. He started using Atari basic from a very young age. He developed a programme for sending messages within his house and this programme was used in his Dad's clinic to make the patient know that their turn to meet the doctor has arrived. This network was known as Zukernet. Writing new programmes was Mark's hobby. After completing his schooling, he took admission in Harvard college and began his college life. During his college days, he developed a site called Facemas. The programme invited suggestions from the students on the photos posted on the site. But this programme was closed after some days and Mark was criticized for using the photos for his site without permission. He also had to apologize for this openly. But his this effort has proved inspiring for him in the production of Facebook. The academy in which Mark used to study had a directory in which the photos and information of the students studying in that academy was stored. This directory was known as Facebook and it is said that from this the name Facebook is given to the site.
The success which Mark has achieved is many times greater than his age. He has brought revolution in the world of web. Facebook has successfully maintained its top position by crossing several levels of offers coming from many big business groups. He has once said in his interview that me and my men are not in need of many but we want to provide best service to the people. Today, Zukerberg is the youngest billionaire of the world. There are 900 million user of Facebook. The effect of Facebook is so tremendous that once a German girl has publicly posted invitation of her birthday on Facebook. The result of which, 1600 people gathered on her birthday party and police force was called to control the public.
Facebook has enabled us to connect with friends of school and college days. We can meet these people daily on Facebook and can participate in their joy and sorrows. Terrorists are also becoming fans of Facebook thus making he police force easy to find and reach them. Nowadays, the employer check the Facebook profile of the candidates before appointing them. Facebook has given the common man the strength to create a social revolution.It has provided a platform to the common man to state his/her opinion openly on various social and political issues. It has also played an important role in increasing internet literacy.
Basically Mark is a drop out of Harvard university. He does not have a degree of any business school. But still he has successfully managed the site of Facebook. The atmosphere of Facebook office is extremely open and free. No one is boss in the office. The employees the enjoys the same freedom as we enjoy while using the Facebook site. The personality and lifestyle of Zukerberg is extremely simple. He is never seen in corporate costumes. The American paparazzi, who are habitual of seeing the high profile lifestyle of the celebrities are very astonished by seeing simple Mark. Mark goes to the market on Sundays like a common man and eats Mexican sandwiches while sitting on the ground. In 2010, a film called The social Network was made on this youngest billionaire of the world. This film bagged three Oscars. He has mentioned topics like connectivity, sharing, openness on his page under personal interest.
The 28-year-old Mark ranks fourteenth in the list of world's richest people. This rich young man is colorblind. Due to this the color of Facebook is blue because Mark has the knowledge of blue color. Facebook has opened its shares for common man on 18th May and Facebook has made profits in crores from these shares. Today Facebook has 1700 employees and its main office is situated in Menlo Park in California. It has its branch offices in 12 countries. The site is absolutely free and the simplicity of Mark has played an important role in making Facebook so easy and free to use. Mark's marriage was also a simple event. He got married on 18th May and only 100 people were invited for his marriage and surprisingly the invitees were not aware as for what they were invited. Such a special common Mark Zukerberg is an idol for the young generation.
Source: Wikipedia
As a holder of an online business, you realize that you have to market your site in the web with the end goal you should create focused on movement. You need to recall that in place for an online business to turn into a win, focused on movement is the key. With focused on activity, you will have the capacity to build deals and additionally keep on increaing the measure of individuals entering your site.
Web advertising is a hard thing to do. You will need to buckle down with the goal you should viably pull in focused on activity in your site. On the other hand, on the off chance that you need a less demanding approach to market your business site in the web, you may need to consider advertising on Facebook.
As a matter of first importance, Facebook is a long range interpersonal communication site that now has in excess of 62 million dynamic supporters from everywhere throughout the world. Most endorsers in Facebook are in the 18-25 demographics. Thus, if your business is focusing on individuals between the ages of 18-25, Facebook is the ideal spot to market your site.
Along these lines, by what means will you have the capacity to market your site in Facebook?
Dissimilar to other long range interpersonal communication sites, Facebook will have the capacity to offer you a great deal of apparatuses that you can use so as to market your items or administrations and additionally your business site all the more successfully and productively. With the amount of individuals subscribing to Facebook every day, you will most likely create a considerable measure of focused on movement to your site.
In Facebook, there are a considerable amount of approaches to market your items or administrations. In Facebook advertising, promoting is by a long shot the most well-known approach to market in Facebook.
Here, you will have the capacity to buy mass flag ads. You can additionally utilize flyers focused to particular individuals. These flyer promoting might be bought for as meager as 5 dollars and it is now offered in the site.
In the event that you are intrigued by publicizing to offered gatherings or advancements, then you can exploit what is called Next Steps. This device might be embedded in your homepage with connections to a comparing supported gathering.
You can likewise install ads inside your homepage's news nourishes.
An alternate approach to promote in Facebook is through informal. Have a go at requesting your system from companions in Facebook on the off chance that they are ready to publicize for you in their system of companions in Facebook. Here, they will be the ones doing the promoting for you by suggesting your items or administrations and also your Facebook profile page and business site to their Facebook system.
You need to recollect that verbal advertising is one of the best showcasing techniques accessible. Attempt to recall that individuals are three to four times liable to purchase a specific item or administration in the event that it is suggested by somebody they know.
You can likewise advertise your items, administrations and business site on the notes segment in Facebook. This specific instrument acts very nearly like a site. When you compose or post something on the notes area, it will be conveyed to the greater part of your companion's news encourages, which could be perused by other individuals. This is an extraordinary approach to get messages over.
These are a percentage of the incredible approaches to market on Facebook. By utilizing some of these devices, you might make sure that you will have the capacity to pull in more individuals to visit your Facebook profile page and let them comprehend what you bring to the table.

How torrents work?
The first question I think someone would ask about torrents would be that how is it different from downloading from anywhere else on the internet. The answer is that the files you download from torrent are not hosted on any one server like that you download from other files sharing sites like Mediafire, Mega etc. When it comes to torrent, first the uploader uploads the torrent file and when someone downloads this torrent file and use a torrent application to download the actual file attached to the torrent the original uploader starts uploading, it's like sending the file to the downloader on the other end. And when a third person starts downloading the same file both the uploader and the first downloader uploads or send the file to this third person and he or she will be enjoying greater speed as two users are sending the file for him. And this process goes on and for popular torrent thousands of people from all over the world will be downloading and uploading the files. So we can say that there are no servers involved in torrenting or there are hundreds of servers as each computer involved in downloading acts as a server as they're uploading what they have downloaded at the same time. So for this reason torrents might eventually decrease in popularity and their health fade off. As people stop uploading the torrents such torrents becomes inactive and you will not be able to download it afterwards.
The best thing about torrents is that you can download at your maximum speed without any restrictions and without paying any money. There's also no restriction of number of downloads or bandwidth here unlike so many other file sharing websites which limits everything for free users prompting people to sign up for their premium accounts.
What is this Bittorrent protocol and clients?
Bittorrent is the protocol used for sending files on a peer to peer basis without the requirement of a server in between. It was designed by Bram Cohen also the creator of one of the most famous bittorrent client, BitTorrent. There are many torrent clients these days and I haven't tried all of them. I've only used three of them viz. Bittorrent, utorrent and Vuze. And some of the most important features of them are.
Bittorrent
It’s a free client which is very much popular and widely used by the users around the world. It has got tons of features to make your downloads fast to organize the downloads effectively as well. It’s free version is supported by ads and if you prefer to remove them you can go for Bittorrent Plus for INR 1,581 (last time I checked) per year. Other features in plus version includes, HD video player, Virus scanning, remote accessing, media converter etc.
uTorrent
uTorrent is much like Bittorrent. But the most important feature they advertise it its small size of about 1 MB. But latest bittorrent is also very tiny (slightly over 1 MB, I think). Other features include auto bandwidth allocation, Remote access from various devices etc. It also have a plus version for $24.95 which gives similar features like in Bittorrent Plus such as no advertisements, HD video playback etc.
Vuze
Vuze is also a very popular client in torrent and like the ones mentioned above Vuze also have a free verion and a plus version. But you file conversion and HD playback is available within Vuze for free version itself. The plus version offers more security which is powered by BitDefender, which is a reputed company, also Vuze Plus comes with DVD burning option (I don’t know how many of us would want that anymore!) and it lets you play files while it’s being downloaded (I think force starting in other torrent clients mentioned above offers the same feature and is available in free version). I like Vuze because it has a very stylish interface. Anyway, I’ve never used Vuze Plus and it comes with a price tag of $29.9
Some browsers like Opera, Torch etc. can download torrents without the help of any clients. But I prefer a client like Bittorrent because I think they can perform faster downloads and are packed with many features since they are designed for the torrent downloading purpose alone. Also, I use Firefox and Google Chrome mainly for browsing and neither of them doesn't have built in torrent downloading capabilities.
How to find and download torrents
So here let me tell you how to download files using a torrent client. First, you need to download the torrent file from a torrent index website (you can do this using your torrent client itself but I prefer browsers). I am using mininova.org for downloading this torrent file. After going to the torrent site you just need to follow the instructions below:
At the navigation bar you have the option to ‘Browse Categories’. Select the one you want or if you are looking for something specific use the search bar.
Select the torrent from the list of torrents you are given and remember to select the torrent with most number of seeds.
From the page you are navigated to select ‘Download this torrent’ as shown in the image and save the torrent file (the size of the torrent file would normally be less than 1 MB).
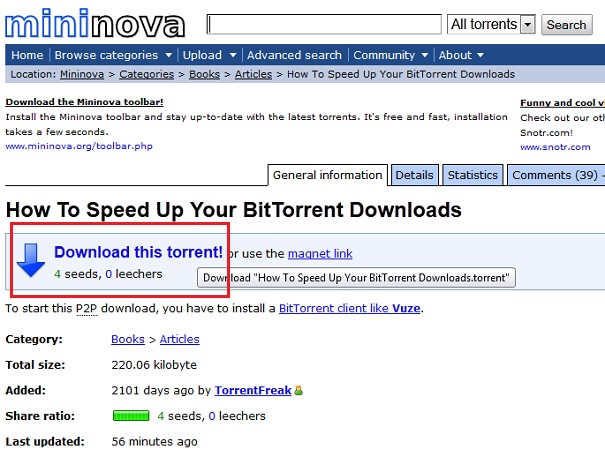
Open the torrent file by double clicking it and Bittorret will open up with ready to download the actual files and you can select the directory where you want to save the file. All you have to do is click OK and wait until the download is finished.
You’ll see a link called ‘Magnet link’ near the the ‘Download this torrent’ (refer to the picture). Clicking the magnet link will directly open the Bittorrent application and you can start downloading torrents right away.
Seed and Peers
Seeds are the people who are uploading the file attached with torrent. Peers are the ones who are downloading it. Normally, you start seeding once you’ve downloaded some parts of the file. At this time you’ll be downloading the parts from other seeds and you’ll be uploading the parts you’ve already downloaded to other users at the same time.
Once you’ve completed the download you can still keep seeding, that is uploading, the file for other people (the original torrent uploader and other downloader appreciate that very much).
When there is very less seed and very large number of peers the download speed will be, obviously, very low and vice versa. It happens when a very popular file is uploaded by a reputed uploader and everyone is trying to download it. But after few hours such torrents seed to peer ratio becomes stable and the torrent could be downloaded at very fast since the torrent is very popular and many users are uploading the files. So it is always better to go for the torrents with the maximum number of seeds. Most of the torrent clients will show you the seed to peer ratio for each download. You should note that this ratio will most likely very low as soon as you've added a file to your download list but if the torrent is healthy then the ratio increases quickly and you'll have full download speed.
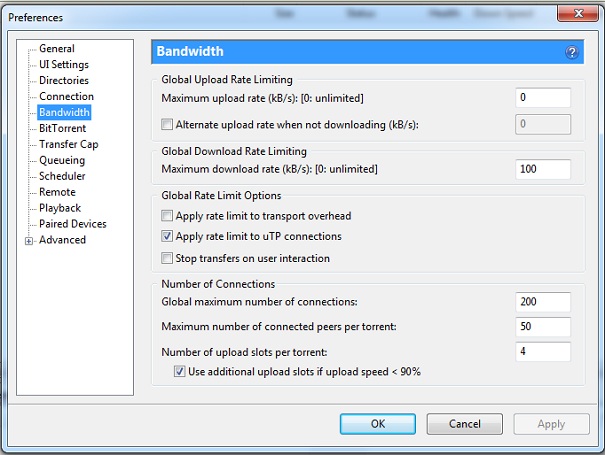
Bandwidth Allocation
If you have bandwidth limitation then you can make use of the bandwidth allocation from the settings to make sure you don’t waste any data. You can set upload and download limits from this window.
For that you should go to Options > Preferences > Bandwidth (In Bittorrent) and make necessary changes. Alternatively, to set bandwidth allocations for individual downloads just right click on the download and select Bandwidth Allocation.
More useful options
Other useful options that comes along with bittorrent are:
Auto Shutdown: It is useful if you go away after adding any file to your downloads. You can use this option to Shut Down, Hibernate, Log off or restart the computer when the downloads are over.
Force Download: Normally torrents are downloaded in parts and joined together. But if you want you can force to download the parts in order, that is from the beginning of the file, so that you can use it even before the download is over. It is useful when your downloading some audio or video file so that you can start playing it even when the download is not complete.
Labels: Labels can be used to organize your downloads. For example you can create labels like Home, Office, Kids etc. and add the label to appropriate download so that it is easier to organize your downloads and find the files you’re looking for in a jiffy.
Search box: Almost all the torrent clients now comes with a search box. You can add your favorite torrent indexing websites to this so that you don’t have to rely on a browser when you are dealing with torrents.
There are tons of other things you can do under the preference window in Options but I guess these are the basic things you need to know about torrents
How to exit torrent client application
Unlike most of the applications your torrent client will not exit after you’ve clicked the closed button nor it will be minimized to your task bar instead it will go to your notification area. So be careful if you have some bandwidth limitation. You should exit bittorrent (or stop all the downloads) after you are done. You just need to go to the notification area (located at bottom right corner) and click on the small arrow which reveals all the programs running in the background and you’ll see the bittorrent icon there, right click and select exit to stop the application from running in the background.
Torrents and Piracy.
Piracy is a growing concern in the torrent world. Unlike other file sharing services torrent doesn’t have one server where the files are hosted. There may be hundreds of thousands computers acting as servers uploading and downloading copyrighted files and it is almost impossible to track them all. There is no one that copyright holders can contact to remove those files. Sure, authorities are fighting it by suing torrent indexing websites who focuses on sharing pirated files. Internet has no boundary restrictions but laws related to internet changes from country to country and this makes it even worse when it comes to fighting piracy. There may be hundreds of websites where almost everything is availableto download free. It doesn’t matter if it’s the Blu ray of the latest movie, software, music albums or television show its all available for free in the torrent world as soon as it is available in the market. And that is what concerns the artists because they are losing money since most people would rather download it free and the only thing that keeps people from downloading it using torrents is their morality. It’s like you are able to steal from someone else without getting caught but you won’t do it because you know it is wrong. There are many uploaders who are very famous and reputed for uploading qualiity pirated content. Most of you would be familiar with name aXXo who once became very popular by uploading DVD rips of hollywood movies. Now the team YIFY is the most popular Blu Ray rip uploader. The interesting fact is that these uploaders does not getting anything for their hardwork of ripping and uploading the paid content as with like many file sharing websites which pays some money for every 1000 downloads or so.
There are millions of free and legal content shared through torrents yet torrents always had a bad name of promoting piracy. The best thing the users can do is to avoid downloading pirated files. Many popular websites in the torrent world are known for the pirated torrent files they share. In fact, it’s piracy that made them popular. Anyway, there are other many websites which are purely legal and which share hundreds and thousands of free content including music, videos and applications.
Image Courtsey
The screenshot and the logo (used in the header) belongs to Bittorrent, Inc, http://bittorrent.com
More Articles …
Subcategories
Web Hosting
Web Hosting is a service offered by web hosting providers to the individuals and organizations to make their websites accessible on the internet. Depending on the requirement, one can avail different types of web hosting such as shared hosting, dedicated hosting, virtual private hosting, cloud hosting etc.
Page 5 of 193