Internet A Growing Need of our Nation, Internet is best option to learn, enjoy, and even earn from it. Internet help students in their studies, a mother in learning cooking, a kid to play games, a man to do official work. In today's arena it is even used for chatting with friends, relatives who live hundreds of kilometers away from us. There has been a steady growth in Social Networking Sites like Facebook, Skype and many more.
But using internet is not so safe, it can even take us on road and can make us a beggar in a minute! Children using Facebook know only how to chat but they don't know who is behind the ID. There are many Black Hat Hackers - ( Hackers who hack for Illegal Purposes). They create fake ID's that look exactly as a victim's friend or relative and extract confidential information from the victim. There is one another method known as Phishing which is the latest way of hacking.
Phishing is a technique in which hackers create a log in page which exactly looks like the official page of Website and they send it to victim and when victim clicks on it they are redirected to " Sign In " page and when they enter the information it directly goes to the hacker and they get hacked!
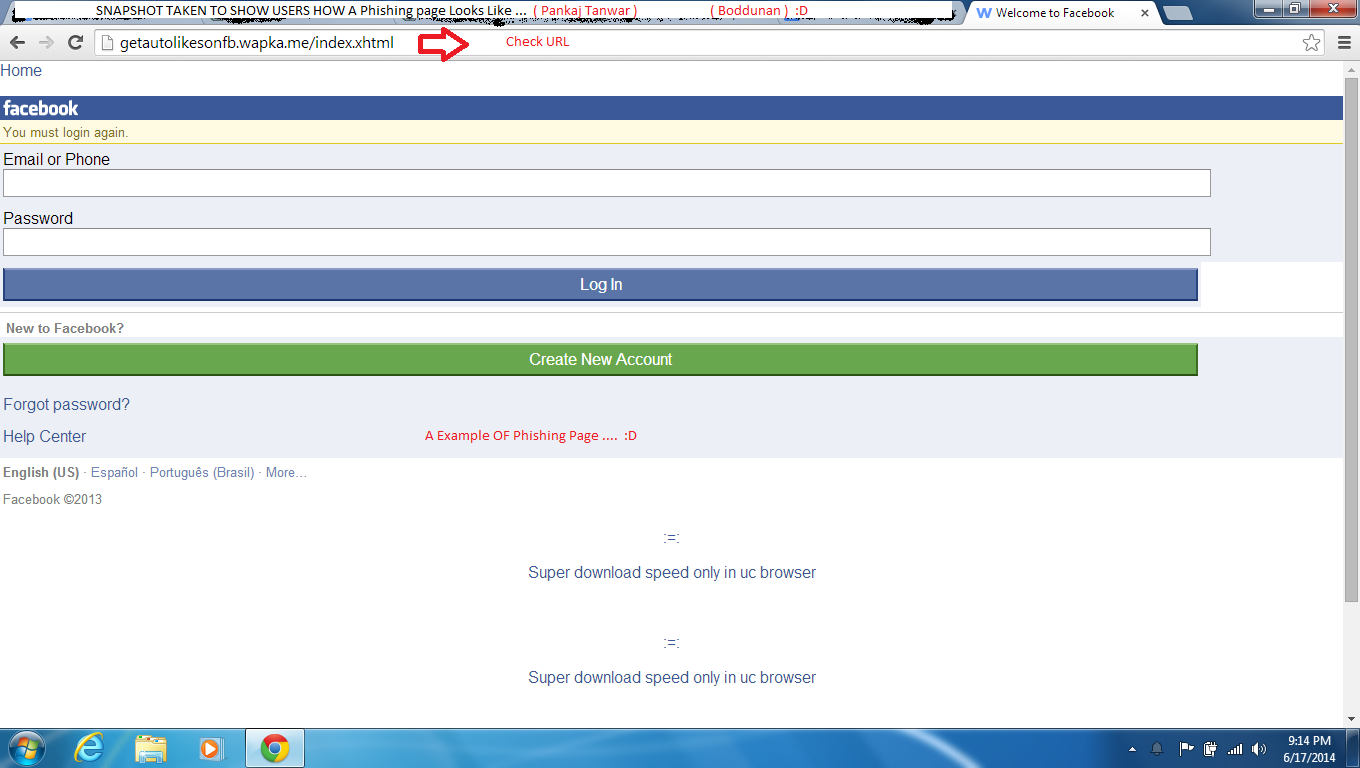
Steps To Be Saved From Phishing Attack :-
1. Always Check The URL of Website you are visiting .
2. Never Click on the Shortened URL ( Like Adfly ) . First Check it then click on it .
3. Never give your confidential information online to anyone .
4 . When You See a Log in Page which asks for your Email ID and Password , always check it's URL from address bar. ( Sometime Phishing page are created just by changing a letter on Main Website . ( Like www. Facedook .com )
5. Always have a Antivirus installed which checks the web pages whether they are secure or not .
Internet is a great tool to learn and explore , but use it in a safe way otherwise you will have to pay for it . This Phishing page can be created of any website ( Not only Facebook ) . It can be created even of Bank Websites and with it a Hacker can transfer all your savings to his account within a second . So Whenever You Come to this type of page - Be Aware and Report it to Cyber Security .
It is Illegal to Hack but if you write your information with your own hands - It will be your Mistake !
Be Safe BE Alert .... !!
Introduction:
The very word, “cyber crime” has several distinctive connotations for system administrators who deal with a sense of sophistication and modernity of integrated systems, which pose umpteenth threats to enterprises which often nipping at the heels of surpassing security of internal environment. There are numerous security tools and programs designed through a large set of research processes aims at building a strong and secure environment for an enterprise to run with superior efficiency and maximum speed within the ambit of organization. Security planning becomes an annual event for each spheres of organization prepares for complete up gradation with the help of security analyzer and security tools meant to achieve superior successes for Enterprise security planning (ERP). With due course of time, the attack methods do change so as the planning and executing of security policy of organization undergoes a complete overhaul from top to button in terms of ambit of security to amend the curve created through different forms of attacks from external sources.
Day by day cybercrimeis becoming extremely critical with a series of black-hat hackers constantly augmenting their expertise in hacking enterprise accounts. Cyber crime is fast becoming permeating and it is spreading far and wide with newer means reaching to unbelievable spheres which many experts have never thought so in their wildest imagination. In the recent past, many big organizations like Microsoft, Apple, and Google have to bear the brunt of the strongest cyber attacks ever which surfaced from time to time to attack from unknown localities. Complicated matters are that these attacks are stealthier in nature which avoids detection for longer times by moving carefully to enterprise system and then remain for longer days and to continue stealing critical information from enterprises without a single person knowing about such attacks. All these create a sense of mistrust due to the sense of anonymity embedded in these attacks.
Sense of ignorance from top brass is bad for overhaul enterprise’s security:
Depending on the survey done by ‘Global state of information security', most of multinational companies (MNCs) are happy with their existing security products. It is then proved the sense of ignorance by top brass of companies in attending complete security cover of organization. It seems they are completely ignoring attacks on their systems which have longer remediation times. An objective view towards security is required to determine the scale of security of enterprises. Due to the speed at which hackers are developing newer technologies, it is evident from their expertise that day by day, they are competent on hacking and cyber attacking in big enterprises. Most of these enterprises till this day are spending very less in research and diagnosis for a completely newer secure environment for their organization. In modern times, sense of security has become a comparative matter. Security of enterprises runs within a clear reference point towards behavioral aspect of security and the mode of trajectory gives a definite level of inference for organizations to know more about possible breach of security in standard security practices. Security maturity model developed by HP entrusts organizations to look for what steps they have taken in order to migrate from risk factors to transformation, prevention and detection of the source of attack points. It empowers organizations to redefines entire security maturity model to check various nodes of attacks in the eyes of the attackers for possible detection through various trespass points. It asks every organization to go for more of an integrated approach and do away all such defensive attack mechanisms. Offensive security gives a sense of proactive security which provides clues of early detection of cyber attacks and most probably find out stealth attacks which buried deep under system settings.
Security maturity model:
The security maturity model empowers enterprises to create step by step processes for complete security of enterprises. Five risk managements have been divided into five ability levels. The middle level is the degree of maturity which is event driven from self-unimagined events. Self unimagined events create out of virtual entities which are perceived as the level of cyber attacks posing from different attack-zones. It provides a sense of virtual reality driven through various challenges posing out from diverse unimaginable zones. Basic tools for security come out from reactive zones, which cover basic level of anti malware products. Layered tools help people to respond faster to imminent attacks such as phishing and stealth attacks. It empowers organizations to delegate powers to the hands of people to react sharply to surface attacks and defuse it before it spreads its wings to different departments of the organization. The third level of security consists of integrated tools that correlate with common management of contextual security environment that empowers users to work with maturity with altered levels of sophisticated cyber attacks. It works in an event driven manner against security attacks. It is perceived as the series of imagined events that occurs at a different set of contextual parameters within a consignment of the security environment. The fourth level of security approach is proactive security which identifies and remediates risks even before it surfaces and it does wait for security updates. It works automatically in retrospective matrices to give security in a faster world. In a world of internet, where everything runs with smart technology; response time for external attacks is very few. These attacks can be controlled through “data execution prevention” (DEP), “structured exception handler overwrites protection” (SEHOP), “Address space layout randomization” (ASLR) and “certificate Trust”. All these methods consist of advance methods of analytics in understanding potential attacks originating from external sources and management of internal system settings.
Defense in depth:
Basic tools of defense consist of perimeter-protection, intrusion-detection that identifies suspicious network activities. Intrusion prevention system (IPS) does not prescribe network-reconfiguration. It is a great technology to protect against dynamic new vulnerabilities. IPS focuses more on specific system settings and carefully guards against each executing processes that include system files, executive files, external application. IPS stops exploit before it is executed. It runs on simple formulae of scanning of all files from booting to load on the operating system. Enhance mitigation experience-toolkit (EMET) from Microsoft Corporation is an excellent toolkit which provides deep penetrative protective techniques that guarantee complete guard against stealth root kit and phishing attempts. All these seem to be good for organizations with a very limited information technology (IT) professionals. There are various malicious exploits in various sophisticated network defense, which varied with various attacks that need immediate attention to enterprise network defense. Enterprise resource planning (ERP) consists of system, network, application and data transmissions. It requires ‘defense in depth’ to continue running on an enterprise network unabatedly and without interruption. For few organizations with interruptions of a few minutes incur can compound huge loss. Android have introduced data encryption for free in its basic models and it guarantees a high level of security. Even if, attackers succeeded in trespassing to database, but still all data there could not be recognizable in terms of bytes due to data encryption of warehouse. In this way, even if all data are lost still attackers will not be able to retrieve the information. BitLocker from Microsoft provides tools for cryptographic processing through simplified encryption key management.
Proactive security tools within corporations:
Log management of the entire set up of system processes provides a tool to review entire administrative security. It consists of log management, log collection, reporting and achieving of different regulatory compliance mechanisms. There are some log management applications that provide various tools to analyze automatically log-set of log collections. In a big enterprise, manual analysis of log collection is almost impossible and there is every possibility of genuine human errors. Therefore it becomes of immense importance that companies should seriously look beyond traditional security models. They should search for a common denominator of security impetus tools which can go beyond basic parameters that can pose vulnerability to different cyber attacks. Enterprise should look for clear integration of different security nodes such as correlation, situational context; integration that can automate analysis and reporting through user’s identity, authorizations, and reputations to protect it from denial of service (DoS) attacks for far greater protection than traditional security tools. There are many potential threats arising out from different sources for substantial business models. Security threat is dynamic phenomena and it needs to be managed and prioritized everyday for smooth functioning of business models. Applications are mostly critical for running a business.
They are the interface of connectivity between company and client. It is mostly vulnerable. Applications are weak links of organization. Attackers exploit critical vulnerabilities within the application and try to gain administrative privilege by explicating different code hijacks surface within perimeters of applications. Proactive security tools within corporations create a complete assortment of applications for vulnerabilities, threat assessment, information technology (IT) governance, identify application vulnerabilities and shut down easy entrance point for attackers. It goes beyond the traditional method of security tools. It scans external points which might pose dangerous for applications. Legacy applications continue to run within organizations and organizations have failed to remove these applications due to incur cost factors. In order to preserve legacy applications, organizations should contact enterprises security solutions provided to top security vendors. They provide speedy delivery of patches even before the original software vendors patch it and send it through cumulative updates. Time to time takes a close look at disgruntled employees who can deliberately pose higher security risks for companies through leakage of official secret information to competitors and hackers.
Watch out for in-house threat perception coming out from disgruntled employees:
Implement predictive security in organizational spheres of financial services and health care. It is important to understand in-house threat perception coming out from disgruntled employees and watch them out closely through monitoring of internet, behavior analysis and strict vigilance of phones and other communication mediums. How much security is adequate? It is important to observe strict vigilance within organization, but simultaneously one should consider deeply about how all these aspects are going to impact heavily on the productivity front. Too much of everything is bad and this one should reconsider these phenomena of what is enough for security. It is wise to compare and engage with further developments that can bring about too many implications and moral high grounds for organizations in times of contingencies. A successful business venture runs with idioms of profit and growth. If both runs with positive sidings it gives greater transparency and further advancements in terms of logistic planning and execution of ideas for possible further developments.
In order to attain these standards; companies need to be agile, innovative and futuristic. Further; all these can be turned into a sense of negativity when companies fail to secure intellectual properties, data, intelligence, services and privacy of customers. Above all; for a successful organization, the top priority is to make one of the most secure environments for clients. Brand of a company is priceless; it builds with time and precision to serve customers through gradual development of customer service managements. If security of privacy of consumers is compromised, then slowly, companies have to face greater risk of reduction of brand image which is irreparable. Enterprise security is slowly becoming a gigantic monster for administrators. Slowly, the perimeter of enterprise security is expanding further towards mobile and cloud computing devices. With the advent of Android, Windows Mobile and Apple, enterprises are offering their services through numerous applications. With the introduction of cloud computing; always on connectivity is providing consumers’ higher time to log in to website and order their products. On the other hand, it is opening wide scale parameters and unlimited perimeters for companies to manage and watch different attacks coming out from anonymous sources. It provides greater challenges and stricter time for administrators to manage enterprises.
Beware of ‘device risk’ of stealing much device information:
Enterprises is now facing troubles from hackers of different kinds such as organize crime gangs, social hacker groups, hackers backed by some countries. All these are professional attackers and they have been funded wisely and healthily from diverse sources. In earlier periods, most of the attackers are from amateurish groups and ill-conceived computer experts. Many rival companies’ spy also part of this attacker’s group. All these threats pose security threats to company. Security threat should be considered in line with the physical and financial threat of companies. In fact, the most dangerous threats of companies from among three threats are security threats which not only bring about financial loss as well as permanent loss of brand ships. Security of confidentiality of customer data is important. Data privacy of an individual is backed by strict legal provisions and companies have to secure these data at any cost. Failure to secure privacy of individuals can make imprisonment for administrators and ending their long terms and strong career permanently. This is important for companies who are dealing with financial records, credit card records and medical records of customers. Multinational companies have to comply with legal provisions of different countries, provinces and local units. Companies should seriously consider in implementing regular compliance audits to determine discrepancies among different units. Mobile devices enable more flexible working conditions and enhance productivity but there are many challenges to monitoring within corporate perimeters. Some bigger enterprises have started creating free Wi Fi zones for employees to monitor activities coming out from mobiles and tablets. Without adequate device protection and knowledge, there is every chance of a free pass to malwares from device use through ignorance of employees. Android mobile devices should have a good antivirus which should be free from the company to its users.
How to minimize mobile ‘application risk ‘:
All these measures have possible privacy implications on employees’ freedom. There should be strict adherence to policies implemented by enterprises for their employees so that never ever such difficulties of implementation of such principles within different spheres of employees will arise at any point in time. There should be stringent instructions for employees to install applications from recognized sources. Many third party applications have malwares which creeps into the system from the domain of applications and pose havoc inside centralized data structure of organizations. In this way, employees can be warned beforehand, by using specific applications for day-to-day functionalities. All mobiles should be connected with wireless access network (WAN) so that strict regulations can be properly implemented. In this way, hackers can be stopped from compromising corporate security. There is difference between corporate data network and cloud service network. When the organizations run within either of these two networks, the nature of security varies completely and distinctively.
Organizations depending upon cloud providers depend heavily on reliability of cloud-based company and physical security of cloud servers. With cloud servers’ organization has always access service and the network remains alive even during strong natural calamities. On the other hand, there are various security concerns for cloud servers coming out from different zones. Organizations can check for procedures, proprietary services, terms and conditions of cloud servers companies before hiring them. It is better to check out for indemnity clauses of cloud servers companies before hiring them for your organization. Organization should control and manage encryption keys and carry out different mechanism to secure data encryption while using cloud servers. Ultimately, enterprises are responsible for security of data from customers and for this they should be extra careful while hiring cloud servers. Various big hardware manufacturers are hiring cloud hosting companies such as IBM (International Business machine), HP (Howard Packard) for seamless integration of data mining within the organization.
A stricter vision control document to regulate internet behavior of employees:
It is important for enterprises to determine clear cut policy guidelines for customers’ cloud services such as Drop box, Google drive. There should be two step authentications for every customer in order to provide stricter security for applications. It is important to block use of consumers’ cloud services. In order to have stricter control over data and privacy controls. There is every chance of breach of confidentiality of corporate information might be hijacked through the use of consumer cloud services. Enterprises should incorporate stricter internal regulations over internet behaviors of employees within and outside boundary of organization. Enterprise must formulate stricter vision control document and every employee should observe and learn about it and should follow these guidelines one by one in order to prevent phishing of data from within the organization. An internal threat poses extreme security risks for confidential security information. Enterprises must look for internal and external threats reflecting upon organization by implementing offline and online mechanisms to stop the intrusion into privacy of corporate data centers. Organizations should make a strict watch on behavior analysis of employees and if it is found any such malicious activities from any nodes of organization, all these can prove to be an indication of disgruntled employees working with evil intention for companies.
Every company must determine a part of their fund for security investments. There should be proper mechanisms and reporting authority within organizations to examine how securities within organizations are working at the behest of security investments. Security funding needs to be investigated in accordance with investment and budget distribution within organizations on a priority basis in order to foresee future attacks upon organization. Many organizations go for software security solutions in order to create a snapshot of an entire server. It is better to go for composite security management which provides a holistic approach to entire IT assets by allocating security funding comprehensively through the process of the mitigation of security threats. Security is a continuous process and every enterprise should not fall behind existing security trends otherwise there is every chance of organizations falling apart due to attacks from all fronts from different hackers. A security assessment of an organization is like creating insurance for the company. It goes on with different level of detecting many of the problems, in finding out trends of security and implementing security policies and detecting various levels of intrusion points to formulate a continuous security policy to enhance security within organizations.
Factors of interaction with external audiences and prospective customers:
Considering the level of protection for electronic data, physical assets, the scope of its perimeter has to be determined. For enterprises, the single most important factor comes out from its perimeters of areas from where the organization and its wings are spreading in works. Detection of organizational boundary such as mobile apps, offline, online, customer support, advertisements and so on are single most influential factors of interacting with external audiences and perspective customers. No one knows in the guise of customer, anytime hackers can gain significance on your system and try to install stealth malwares to steal important confidential information. Every open node to communication can be termed as the perimeter of the company. Strict measures should be deployed in order to have proper care of enterprise’s administrative and data units. Even in ancient times, when there is no computer and no concept of saving electronic data, still that time valuables are kept within the boundaries or underground in order to keep out from prying eyes from lurking into.
Now, there is pretty much importance attached with data and its security and day by day there is vast increase of flow of data from amongst various sources such as social media marketing, information sharing, information gatherings, and smart phone cloud services and so on. Attacks are now becoming faster and sophisticated; there is urgent need to establish strong and continuous security mechanisms for organization. Many organizations are spending lavishly in keeping perimeter of organization safe and secure. Continuous analysis of logs of administrative process gives proper detection of abnormalities from within the organization and in this way the entire functionalities can be thoroughly checked in and grudge and rogue elements can be checked before it is too late for organizations. Most businesses are throwing a huge sum of money for security at the perimeter of an organization, but they are not making thorough attention to the internal security of the perimeter. According to research once hackers intrude organization, the average time to exploit data center is 416 days. It goes on to show. Organization has far greater response time to secure internal security from within its perimeter and for this it is essential to create sustained and strong security mechanisms from within enterprise limits.
Actionable security intelligence to investigate and create research within organization:
There are numerous schools of thoughts who are presuming an alternative approach to secure entire information technology (IT) infrastructure. It advocates, constructing of a proactive security measures in order to attack hackers from the point of execution. It aims to go beyond the traditional method of security and wants to search and destroy malicious codes from different segments of the Internet before they are completely distributed. Every organization should have in-house security investigative agencies to find out information about persons or organizations who are giving away something to uncommon enterprises. Enterprises must have a confidential report about such people and it is duty of every organization to black list of those people and in this way, spreading of manual information gathering through professional stealth hackers can be assimilated before they actually happen. All these attempts need superior security performances such as reports, infiltration, approach, discovery and capture. All these are a series of processes which every big enterprise must obey and carefully follow in order to spread security network from beyond the boundaries of an organization. This approach needs to be based on intelligence gathering and research. It needs proper identification of different entry points and behavioral analysis of individuals and competitive organizations.
Scanning of peer-to peer network can reveal information about individuals dealing with scams. Fraudsters and phishing attempt and can reveal more information about them. It needs actionable security intelligence to investigate and create research within the organization to find about different spheres of security which can have alternative spheres in determining different forms of actions and reactions. Organizations should always be concerned with every indication of abnormalities and should straightforwardly find it about the way to see the entire sequence of events. It is a continuous way. Enterprises should observer networks across the Internet in order to stay one step ahead of the attackers at any cost. Many enterprises run with “zero day vulnerabilities” which can be experienced with various software flaws in applications and server. These security flaws can lead to cyber attacks and compromise the security of an organization. Enterprises needs to install software from reliable software vendors who are releasing time to time software fixes and culminating updates of “zero-day-vulnerability”. Think twice before installing multimedia flash and Java products which are marked with perpetual software-vulnerability. All these next generations’ data flows should be carefully followed to find out the real perimeter of organiza.
Concept of bring your own device (BYOD):
Information technology infrastructure has paved the way for a safe passage route for many security experts. They think of it as the golden opportunity for administrators to track employee’s behavioral patterns through certain distinct administrative principles. In every organization; there are many such rules which may intrude individual privacy but can become a boon for the enterprise to be a watchdog for administrators to scrutinize behavioral patterns of employees. It is the concept of “bring your own device” (BYOD) which empowers individual employees with continuous connectivity which works in favor of increasing productivity as well as continuous surveillance on the part of system administrators. In the earlier phases; companies do not let their employees to use mobiles while at works. There are strict vigilances on the part of companies to do away with such practices.
Sacred information:
It is important to convince employees to shred some part of private information such as sharing of profiles and logs as these should be considered as “sacred information” for betterment of security of organization. All these settings should have administrative rights and employees cannot alter and change it on their own by using their mobile devices. In this way, the whole set of infinite data flow towards corporate networks can be easily managed by a different set of data restriction policies and identical data can be revoked in order to streamline network servers. In this way, enterprise does not have to invest heavily on mobile devices, as with implementation of BYOD policies, enterprise can get back a huge sum of the return on investment (ROI). So, all these mobiles devices need to be incorporated into BYOD policies and owners should be strictly informed about new set up rules and policy guidelines implemented by organizations from time to time.
Some drawbacks of BYOD:
Simple neglect in implementing these policies can bring about mass exodus of corporate data to outside agencies. You are never sure how this information could galvanize and disappear from corporate network possibly through different mobile channels. A simple auto synchronization options in email client within mobile operating system of an individual user can send out a large chunk of corporate correspondence to separate servers. With the advent of Android, everything is currently in the cloud and with newer auto synchronization feature every part of data is being synchronized continuously without user’s intention. All these are vital drawbacks of BYOD and corporate leaders should segment corporate and native data and should use stronger encryption mechanisms in order to protect data even if they are approved by attackers.
All devices should be configured over the air to maximize speed and efficiency of discrete devices. Over the air configuration is done through direct Wi Fi or Wi Fi connectivity which keeps a vigilant eye on users all the time. Data generation points such as virtual private network (VPN), nearby devices, native application and general data sharing applications aims to secure corporate documents and content with a string of information already embedded within specific information from input of company’s affairs. With the advent of mobiles and increase of perimeter of organizational business, time required for wireless single and uniform wireless connectivity among different segment of employees. In a company, there are different sects of employees such as office desk, marketing, services, logistics, human resources, information technology and so on and all these employees are difficult to connect through intranet. For example a common software or data usages policies should be established from among all units of the organization and these should automatically warn employees when data usages limit is reached. In this way the organization can throw stronger data security policies to drive out other forms of misuse of resources from within the organization.
Creating a sustainable economic model of development through proper BYOD policy guidelines:
It is wise on the part of the corporation to provide self-service to employees in certain administrative functions. It works in both ways. In the first way, it reduces the number of basic administrative functions of system administration by minimizing lagging time from within the organization. Secondly, self-service such as resetting passwords, when the password is lost, introducing geolocation services for lost devices and able to wipe out data of lost mobile remotely so as to minimize time of response time of hackers to steal data. If these functions are not to be provided with individuals than in the case of stolen mobile, they have to report to the administrator and this takes huge time and during such case, time factors are significant. In this way, employees are empowered to function certain precise administrative actions which are good for the corporation in case of such urgent times. Otherwise employees will be limited to use mobile for “emergency call only” functionalities. Proper BYOD (Build your own device) policies not only save corporate data from prying eyes of hackers, but also make it safe and through implementations of constant security software and security practices. In this way, administrators have clear cut power over corporate data within mobile devices of employees. Administrators can seriously wipe out all relevant corporate data from outgoing employees’ mobile devices. Even if you are not paying for internet, still you can track employees’ geolocation.
Stop misuse of BYOD from within organization:
There are so many paid applications which some workers do not wish to buy it. They jailbreak Apple devices or root Android powered devices for installing paid application for free. Jailbreak or rooting of mobile devices lead to opening of the flood gates of malwares into devices and this can be dangerous for security of corporate data. Administrators should detect such devices and should wipe all corporate data immediately from the device in order to stops malwares from entering into the system. With the advent of Apple and android, users can easily install additive game like “temple run” and use it as office hours. Administrators should carefully look these behavioral aspects of specific employees and delete such time wasters before they spread into different segment of behavioral patterns of employees. Time to time, Android and Apple updates operating system and warn users to update it. It is up to the discretion of users to update at their convenient time. In this way, corporate can look beyond and find about pros and cons of different set of newer functions and can check and verify whether such devices would have better use for employees for better implementation of BYOD. With the advent of BYOD shifting of purchasing and managing devices come under employees as this can create a proper sense of the return of investment from among employees. It eliminates the cost of device purchase and management of devices. In this way, company can offer better network management functionalities to its employees in order to create a continual connectivity.
The role of integrated systems and big data analytics to create work-load optimize system:
The principal process of acquiring, retaining and growing customers is as ancient as the beginning of commerce. During ancient days, when there are no monetary exchanges for business transactions, in those times, performance based exchange method such as the barter system was put in place all over the world. It creates a long standing bond between consumers and many customers it becomes a bond for generations. Creations and retention of faith in these exchange services are paramount and this principle is viable even today without any mince of words attached. Greek philosopher Heraclitus said that "You cannot step twice into the same river". It is said even today for enterprises when they opt for various security solutions. One needs to consider inward and strengthen all possibilities to inculcate virtuous traits of successful security solutions and bring back in a united manner so as to make every aspect of organizations secure and safe. The channel of communication has been on the rise from manual conversation to internet, social media marketing methods. Customer expectations from enterprises are on the rise and in these enterprises need to evolve and create a sustainable maintenance of the server and reduce log in lagging time. It does include the advent of workload optimized system to adjust itself from a different set of heavy demands from consumers. Generally, too much security spoils the bean. But enterprises have to implement a sustainable security measures in their integrated systems, in order to preserve privacy and data. Access security measures slow down the server and incidentally slow down response time.
It does not augur well for bigger corporations. Workload-optimized system with an effective technology provides perfect analytical solutions. The role of integrated systems (IS) in analyzing big data analytics (BDA) goes through the latest technology trends compiled with customer analytics make a leading work-load optimized system. Addition of business intelligence services, security framework, broad band networking, BYOD and business and customer analytics, enterprise log files, makes a fact sheet of external and internal events based on the appropriate distribution of different services. It creates scope for innumerable unchallenged opportunities for organizations through deployment of business analytics from the tangible benefits arising out of exceeded expectations. It secures all viable routes of consumer transactions through proper implementation of diverse security ideas and speedy performance improvement. In order to improve better customer relationships management;, organizations vouch for a different set of ideas and channelized different behavioral aspects of customers in order to improve personalized interactions. Consumers are not homogenous; they show distinctive traits such as patients in case of a health care unit, students in case of educational institutions and so on. Through the acquired process analysis, enterprise can prioritize the need for consumers and can set numerous agendas as a result of such tabular distribution. Through this behavioral segmentation targeted consumers can be reached out and served better through unique custom-made solutions. Brand awareness is the biggest challenges for enterprises. The nature of most business shows most companies is more over searching for any opportunities to stay ahead of the race from amongst different competitors. They can get to any such extent to reach any point of surpassing market leader of any segment. For this, it is essential for enterprises to adopt a stern but system optimized security solutions.
Conclusion:
Organizations can be a significant contribution in educating its employees and enhancing their technology-knowledge beyond any boundaries. It creates a secure system as workers no longer feel alienated and they know if they work for good then they will be felicitated with more monetary increments and for this the manual security breach of company remains null and void. It makes a scope for new found expectations as a result of all these incentives the security perimeter of organizations slowly becomes a prohibited land for external attackers. Slowly, the company adopts employee first approach and creates virtual cooperative units from amongst different segment of workers. This builds trust and confidence among employees and they go for complete success by going for extra miles in securing maximum profits for the organization. These enterprises are known as social enabled enterprises and it creates trust from within and that becomes embedded within the organization at different spheres of life and interaction with customers.
Every employee becomes a watch dog and stops any such malicious attempts by intruding basic security organizations. Social enabled information technology supports languish a positive outlook on enterprise and it creates a community driven security parameters for all walks of enterprise. Organizations are keen to harness power of big data. If above mentioned security measures are not considered seriously than the value of big data remains null so far there is a proper implementation of strong security for data on individuals. Effective information integration and proper security governance protects sensitive information which is part of big data servers of enterprises. Data protection is supported by law. Sensitive data are everywhere. Data in systems are being used by many third parties. Security concerns arise from data transmissions. These are few security fundamentals which most organizations should adhere to and go for implementing in their own customized approach in accordance with critical business operations and reporting.
Ethical hacking and its opportunities
Ethical hacking means hacking a system or a website for to understand the security weakness in order to make the system or server safe and secure. Ethical hackers are good hackers they are known as ‘white hackers’. They find vulnerabilities or security weakness of a website or a system and report the issues to the concerned authority. Now ethical hackers are more in demand than other hackers are. Many famous companies like Facebook, Microsoft, Google, Paypal etc were providing some cash credits to the security researchers for finding vulnerabilities in their products or website. The cash credits start from 500$ to even $1, 00,000. This kind of appreciation from different companies is encouraging more and more programmers to come into the field of ethical hacking.
What ethical hackers do?
They do security research on various topics. For examples: Bypassing windows is a security vulnerability, deleting a photo or updating a status on behalf of another user without their access is a security vulnerability (social networks), taking a private detail of another user or making changes in the server or file of a products without having the administrating access is also a security vulnerability. Concentrating on a particular features and doing various researchers in order to exploit it may help to find vulnerabilities. We cannot guarantee that whether there is security vulnerability is there or not but if there is anything then they can find it by doing security researching. Usually ethical hackers begin with general exploiting techniques like CSS, SQL infection, remote code execution, buffer overflow etc. Starting with this kind of techniques will help the hacker to know the security status of a website.
Tools for ethical hacking
Generally, hackers use Brutus, a kind of software that helps to make login attempts by looping or password dictionary attack. There is much other software like this are available in the internet. Usually elite hackers create their own software for doing hacking or for security researches. Inspector, a kind of tool that is now available in the browsers like Mozilla Firefox, Opera etc. This tool helps the programmers or the hackers to see the html/javascript code of the page and the widget code. In addition, this allows the user to make some temporary changes in the web page. Google dork is also a way to find infected sites. Remember our goal is to make a safe computer world. All the best!
How to stay secure?
We hangout with laptops and smart phones on a daily basis. Every right implies a responsibility. Every opportunity is a possession of an obligation to the form of obligation. One is in charge of the security of one’s own laptop and smart phones. In the dynamic world of digitally encoded electronic transmission of mass communications through storage and processing power of computers, changing face of internet and fast-paced computer programming creates limitless space for hackers to promote nasty works. No computer system can be secure. On the contrary, a system with high security makes a paranoid situation for users. Computer is designed to cut down lagging time in day-to-day operations. The popularity of mobile devices has created a brilliant line of hackers. What should be a seamless approach to get rid of viruses from your PC and smart phones stroked with malwares? In this article, we will figure out how some simple lessons one can learn to destroy viruses, Trojans, spywares, key loggers that do not need administrator privilege of your PC. Do not get lured to different tactics of malwares and other nastiest of internet. It is best to be securing than sorry. Your computer needs preventive health care.
Preventing infection is better than post infection scenario. One just has to move beyond traditional security to modern security set up.
Before advent of “Windows Defender” from Microsoft, users have traditional security measures on their PC and smart phones. It is free at genuine version of Windows. It is a multi-layered security set-up. Most folks protect their PCs by using multiple signature scanners based on anti-spywares, anti-viruses, anti-Trojans, anti-root kits. For most folks, the cost factor associated with anti-malware suite is beyond purchasing. According to many security experts, multi-layered security could not be better than single prolonged approach of security. Multi-layered security does not provide additional level of security. It is heavy on system resources. Many-a-times some definition modules collide conversely with different definitions modules to stop all layers of security parameters. It results in a blue screen of death (BSOD), destruction of critical boot files and computer stops response. Multi-layers of security pose heavy costs in terms of financially as well as performance and health of your PC. It creates complex security architecture and can delay launch of application on to your PC. There is no such theory as 100 percentages of protection. A good antivirus suit can only manage utmost 90 percentages of PC security. Multi-layer security increases processing level of the central processing unit (CPU) to a critical level so that slowly it will gradually reach towards law of diminishing returns.
What is wrong with multi-layered security?
In a multi-layer security, an aggressive security product of a particular layer can overlap and attack security of an additional layer, resulting curfew within existing security products. Renowned security products from renowned security vendors can resist rogue security applications and self-protect to survive these eminent attacks. Sadly, but true more and more advanced methods are developed by hackers in which they are able to turn off existing security products. Microsoft began collaborating cooperation among diverse recognized security vendors to create a cohesive unit of security products with timely updates in order to overcome the presence of hackers. Now, it is clear, no security product is self-sufficient and for this it is better to take a preventive approach to security with moderate computing practices. If someone is deliberating browsing malware ridden websites with a security suites, then do not provide that security programs to resist termination. Rarely, security programs can catch hostile agents.
The world of hackers:
The world of hackers is treacherous but fascinating, but it is the worst situations for ordinary users who are mostly ignorant of safe computing practices. This article is a matter of safe computing practices which is better practice of employing multi-layer of security. Hacker is faceless with attitude of trespassing computers. It attacks your computer from a far away unknown distance and intrusion without your permission. Hackers chose to operate from a land which has no legal liability and restriction. They are code-jockeys with a miracle bit of programming expertise. Hackers have not always been bad people. There are white-hat hackers who boomerang vulnerabilities and exploits of a computer with the same fitting precision reply to attackers. They can detect the exact location of black hat hackers and can reverse-engineer the same hack to hackers. White hat hackers are used in governmental as well as private enterprises to investigate vulnerabilities in data center and find security vulnerabilities and suggest critical patches to secure the system from zero day vulnerabilities. They fight with black hat hackers and just try to minimize the risk of exploitation from them. That is why; white hat hackers are called ethical hackers.
Black-hat hackers gain sufficient administrative privilege to enter into vulnerable enterprise system and control entire administration from remote. Black-hat hackers are called “crackers”. They spam mails, steal classified documents, gain administrative control over network computers and smart phones, snoop around inbox and social networking accounts through the process of electronic civil disobedience which has altruistic motives.
Android as smart phone operating system:
Android as smart phone operating system, become immensely popular within the shortest possible time that attracts hackers to lurk into your mobile operating system and steal valuable data as well as your online identity. Few years back, “DroidDream”, an android malware existed at “Google Play Store” formerly known as “Android Market”. Since then, Google has comprehensively changed application introduction policies of “Google Play Store” with a virtual platform of testing of apps. Since introduction of “Android Jelly Bean”, all application runs within a virtual environment which runs parallel with android operating system, which is critical of security of system files of Android. Android is an open source Linux operating system well supported by Google. Rogue applications, spywares, malwares and application with privacy threats are fired from “Google Play Store” entirely.
Major antivirus vendors offer mobile antivirus for android. Gone are the days, when mobile antivirus drains batteries completely. They stopped to web based., malwares, phishing and scams, drive-by-downloads, browser hijacking. Some major network threats reach due to multiple network capacity of innovative smart phones. They have provision of tethering, mobile hot spot, direct Wi-Fi that can slow down data transfer within Wi-Fi traffic. Not only, it incurs financial loss but also complete loss of all isolated and classified data.
Few suggestions on Android mobile security:
1. A Google account with Android lets you organize and access contracts and synchronize and back up everything. It allows you anywhere access control, keep your stuffs secure. With this account you can automatically use other Google services such as “Google Play store”, “Google Books”, and “Google Music” and so on.
2. Set “Screen lock” on your android device. The screen locks when your phone goes to sleep. If “Day Dream” is enabled, screen lock does not work.
3. You can encrypt data on your phone. It is irreversible. It provides additional protection to data when your phone is asleep or stolen.
4. Encrypt external SD card. It will ask the password that is required to decrypt the device each time you change it on.
5. “Set up SIM card lock”, to receive SMS (short message service) to receive SMS notification to another number when SIM is changed. It will charge normal SMS cost.
6. Do not grant “Device Administrator” in “Android Device Manager” to unknown apps. When a phone is lost or stolen, through “Android Device Manager” it can be locked remotely or entire data can wipe out from device from web representation of “Android Device Manager”.
7. Do not allow installation of applications from sources other than “Google Play Store”.
8. “Verifies Apps” functions warn users before installing applications that may cause harm or damage-device.
9. Use trusted credentials such as CA certificates or internal installed certificates from the device manufacturer.
10. While installing a new application carefully reads “Application Permissions” of device.
11. Android as an operating system is expected to be very secure. It opens up source Linux mobile operating system. Android operating system trusts you the user and the community of developers.
12. Android offers you a lot of power and with power comes responsibility.
13. Android works with multiple layer of defense, starting from “Google Play”, “unknown sources”, “install confirmations”, “Verify application warning”, “Run time security checks” and finally the newly introduced “Sandbox and permissions”. Android has multiple layer of defense to protect against malware incursions.
14. Android has defenses to be protected, not your data. It is preferable to implement cloud-backup solutions from Google or other third party cloud services.
15. Do not install anything and everything from anywhere and everywhere.
16. Keeping your data safe can be more about taking common-sense steps to minimize data loss risks.
17. A review of one star rating in “Google Play Store” is a sign of something wrong. Do not install that application from “Google Play Store”.
Safe computing practices:
Internet resides within web browsers. An outdated and vulnerable web browser can make your entire computer susceptible to web. It is a gateway to the Internet as well as to worms, hackers. It is still a nice idea to use updated web-browser. With it, you will be in a position to protect your data, privacy and security and consciousness. If you are running Adobe Flash, you should modify “flash player setting” and disable third party flash cookies. Flash cookies never expire. It continuously resides inside system setting. It sends anonymous browsing behavior, internet usages statistics and basic computing practices to concern website. It is better to live without “java”. Uninstall it from computer. In Windows 8, go to “charms menu” by going to lower left corner of desktop and click on “search” icon. From their search for “nPDeploy Java1.dll” and removed it from system drive (generally Drive C). After inactivation, “Java” leaves these files and this can cause its identity theft.
1. Keep Windows and MS Office completely up-to-date by applying the latest fixes from Microsoft Update-Service.
2. Ensure that you regularly update third party applications, web browsers, Java and Adobe Flash.
3. Recently, Microsoft Windows, integrated updates of Adobe products in its cumulative updates. Turn “automatic updates” to automatic to receive these updates as soon as Microsoft releases it from its server.
4. Stay away from malicious sites which offer commercial software for free, key generators and other packed materials.
5. Avoid accidentally logging into hostile sites by installing “WOT” or “AVG Link Scanner”. These are the free browser plug-ins.
6. Download files from trusted sources. Scan external media through free online signature scanning service like “Virus Total” or “Jotti”.
7. Install a good firewall. It serves to protect against worms and hackers. You should not turn off “Windows Firewall”. It will keep your PC safe from vulnerability of worms and hackers.
8. Before allowing an application to receive information through the firewall, do not forget to understand the inherent risks involved in it.
9. Windows 8 has built-in “auto-run” disability function.
10. Use Windows 8 with a standard user account.
11. Enable Windows 8 Family Safety for a standard account. It controls website that users can access online. Set it to “Online communication” in web restriction level. In this segment user can view websites of general interest, social networking, web chat and web mail categories. Adult sites are blocked. Administrator can edit “Family Safety” to “block file-download”.
12. Turning on “web restrictions” with “Windows 8 Family Safety”, automatically turns on “Safe search” setting of Bing, Google, Yahoo and other popular search-engines. In this way malicious websites are blocked while searching on popular search-engines.
13. With a “standard User Account” on Windows 8, one can run Windows with limited user restrictions. It runs all high risks program with limited rights. Programs with limited rights are handicapped to change basic system settings.
14. It is a bright idea to prevent malwares from entering your PC. Standard account of Windows 8 reduces privilege of programs which seem a workable solution for most users.
15. If one has wired connections, it is best to purchase a physical firewall. Router is better known as a physical firewall. It is preferable than a software firewall. Hardware firewall does not consume system resources. It works beyond computer.
16. Image your main drive to an external back-up drive.
Enterprise computer security policies:
In the last decade, use of personal computers has expanded exponentially. Due to the advent of this technology, there are huge gains in productive capacity of employees. The principal aim of a reliable computer system is to control access of users in relation to the release of data. This process is a correlation between subjects to objects. The security policy aims at managing a set of rules related to general goals and objectives. The computer security policy creates defined determination of organizational policies to streamline different ways of accessing of data. A static and a comprehensive security policy must interpret general policies accurately. It must stick to laws and regulations and generally acceptable standards unequivocally. Confidentiality of policy states that administrators have a right to observe classified documents of the organization. Integrity policy refers to the amount of quality of data saved to the computer. It should reflect statistics of people. Data mining must be in accordance with proper distribution and management of data. Unorganized datum means wasting of infinite degree of information. Integrity policy must reflect a considerable amount of research activities which should provide proper information management inside core wings of the organization. Properly authorized officials with a high degree of integrity should be located in a position to access data with considerable sense of security. Due care must be provided to ensure the physical as well as manual safety of data. All these should give proper security management among all these people of the organization.
Unauthorized persons should not trespass data of an organization. Organized unauthorized access of eccentric individuals can slow down the entire server and the actual user will find it difficult to log in when it is necessary, due to the extra load of shedding of server, which could break the entire network architecture of an organization. Availability policy of computer security makes a time frame within an organization where curfew of server time and time available to users is properly cared for. This reduces extra load on server times as well as it sets up a sense of fitting safety through software restriction policies. In this way, it should cater to the basic need of computer users by providing them absolute time when it matters the most as well as providing users the most essential part of clean computing where as public as well as loading capacity on different third party vendors can be restricted. Proper management of server can give a complete full proof security to server which would not be bogged down through perpetual virus attacks as well as continuous security vulnerabilities.
In theory, there is infinite difference between computer security policies and related theories attached to security management of computers. Principles are configured for inclusive accepted standards of conventions which are nearer to a proper set of policies. Security mechanisms are established from a predefined and designated set of security principles. It all goes through the set of inclusive standards of accepted principles which are almost practical and apt to serve basic tenets as well as respectable understanding of organizational security principles. These mechanisms are originated from individual as well as collective behavioral aspects of organizational principles. Security principles create “access control” which prohibits illegitimate access of unauthorized users and also access to authorized users in non-specified time intervals. There are two forms of “Access Control”; administrator and standard user. Administrator has right to access into unforgivable “Capability”. “Capable” is an incontestable proof of authorization. Here, administrator can over see entire functionality and can stream line all set of events into actions by sending proper and inconceivable management of delimitation of powers to standard users. Generally, in a complicated organizational networking environment, many sets of interconnected nodes have different access rights to different individuals at different time interval, which can clutter all those access rights of users by clogging them into a set of “Access matrix”.
Access matrix and least privilege mechanism:
“Access matrix” is not a real time behavior of computer security principles. It is a virtual representation of all access rights which are many times cluttered with each other through the principles of veins inside the formation of mind. It has numerous sets of independent yet dependent set of control mechanisms which can control and delimit other set of actions and access controls. Administrators have access rights to properly manage all these actions with similar and prudential back end servers. It could create a huge amount of memory usages due to flow of large amount of access-requests all around organizational security network. This creates the concept of “Access matrix” which distributed a different set of access rights and stops heavy users from stopping all other network-connectivity. Security policies of organization do include physical security of network server as well as functional safety of this Server. If it is not been controlled, in the long run constant heavy requests from a different set of users through access points can destroy hard drives of Server. It creates typically predefined structures from the existing norm of organizational security policies, which are popularly called as “least privilege-mechanism”.
SAP:
System administrator in an enterprise is called as “subjects”. Standard users to whom administrators distribute and delegate access rights are called “users”. Subjects have the right to delegate and restrict power to users. When that management comes down to user level through the process of delegation and restriction parallel focus of administration comes to light. It is called “special access provision” (SAP). SAP is a part of “least privilege mechanism” (LPM). The principal point of action here is to control access rights of millions of users. Access-matrix shows them as the account is not there and it behaves to users as if existence of particular email account is not there, but it is there inside deep “user setting” of administrator and can only be accessed by user through correct “user name” and “password”.
2-step verification:
Further with due course of time hackers through the process of social engineering able to detect “user name” and “password” of users and then can indict continuous log in to unstable network server. Google updated organizational security policies to a newly introduced and conceived “2-step verification”, process. It is a security of your mail as well as on Google server located in an undisclosed locations. This security process involves the presence of hardware which in turn asks hackers to log in from that same hardware such as computer or smart phone to log into mail or other Google services. It is easier to hack into software security system which has a virtual presence. With “2-step verification process” Google ensures the presence of reality such as hardware to be logged in mediums and this out rightly obstructs hacker’s attempt to “brute force” user Accounts. User has one more security option to protect and safeguard personal information. When the bad guys steal your account’s password, they could not lock you out into your account as they will require authentication code from your phone.
“Realm of knowledge” is always secret for functional reasons and it differs from person to person. Man is a rational animal. Its mind differs from situation to situation. Like five fingers of us are not same, the similar happens to different personalities. Network security of enterprise deals with “realm of knowledge”. These are classified and secret documents of organizations and access rights to these documents are extremely limited. Even these secrets are being kept with fewer people and from generations these secrets have never ever been shared with outsiders. Computer helps us to stay connected with modern world. Web browsers, help us to log into the Internet world. Computers are fast becoming personal assistants of us and it is needed in day-to-day activities. Most of the time we tend to depend upon smart phones and computers all over the time and want to be connected with rest of the world. We trust them more than personal assistant and save most of the data and private information and want to believe it always be safe and stays secure.
It is pertinent to have a secure smart phone and computer environment in order to save important data with outstanding private care. According to statistics, the use of internet with smart phone devices has doubled within a year and this goes on to show how people are smartly using internet for smart phone devices to back up all of their information into cloud. In this way, if attackers have access to your mobile and erase all data, still you can regain control over all data through the process of cloud and can download and retrieve all of these data easily. With the latest update, Google Photo can now back up all videos stored inside phone and this will create a complete back up of all of your multimedia contents. In this approach, hackers will not be able to gain advantage of unsafe computing practices and vulnerabilities in a secured and patched environment. They cannot implement and inject malicious codes through the process of reverse engineering to leverage point of attack through spreading of distinct layers of malware invasion.
Infamous Conficker malware attack:
One of the worst malware attacks in the annals of the Internet is the infamous “Conficker” malware attacks of 2008. This malware spread in each nook and corner of the world and affected millions of computers. It spread to many computers and many home users as well as enterprises and networks got affected with this worm. It benefited from the advantage of Windows to gain control of its administrative privileges and installed small files to complete control of computer. It disabled auto run as well as in built antimalware in order to create a safe environment. It captured the home network and by using bandwidth of one computer it affected a different set of computers and slowly it created its network all over the area within a few seconds. It disabled automatic updated and changed system time in order to avoid “day-light saving time”.
This infamous “Conficker” worm spread across the internet, due to ignorant users who had not practiced safe computing practices. There are no shortcut rules and there is no security software or security policies which will cut short worm attacks on computer networks. It should be a cumulative approach of safe computing practices coupled with a strong sense of observing a decent knowledge about operating system in which you are dealing with can prove to be a strong point to fight it out with worms and other related malware problems. Slowly, with all these necessary awakening proper establishment of security as well as safety practices, home and network computers will soon be full proof from all nasties of internet. Internet is not a civilized world. It is a world of jungles coupled with anarchy and indecency. There is no way one can establish the law in these locations. Internet runs beyond boundaries. There is no way one can sketch country specific limits to it.
Proactive protection:
When we search something on Google search, the server can be somewhere at the North Pole in an undisclosed location where even many people from Google know it. So, if India makes a law that only those websites which are located in India should be accessible by citizens of India, proves to be a mere fallacy. Many website are hosted somewhere but they run at some other places. For this in order to control the Internet is a very difficult subject. Users have to be aware of these misconceptions and outlandish behavior of internet. Once you are connected to internet thinks that you are entering into a deep jungle. Internet is not a place where democracy and rule of law associated with it. For this one has to be better equipped while entering in these deep and dense rooted jungles. You cannot guarantee even if you are well equipped with all these safe protection to be safe after entering into it. Similarly, you cannot guarantee of safety and security of data after connecting with internet. Someone could argue they have anti malware and other forms of modern layered protection and they will not be afraid of such imminent dangers. If they think so then they are at the wrong way and with which they have to think of proactive protection.
Only humans can perform proactive protections. No security suits would do about it in the wildest stretch of imagination. The internet is a network of networks and it is impossible to know the exact location through which a computer is connected with. If that server computer which you are connecting with for internet browsing is full of malwares then for sure you are being affected with such malwares if you are not practicing safe computing practices in the truest sense of mind and heart. Here, are few guidelines to observer to secure your personal computer.

How to secure Windows 8 PC?
1. If you are Microsoft junkies, do not forget to get Windows 8. It should be your clear choice and be sure to obtain the 64 bit version of it.
2. Have a motherboard that supports secure boot. Secure boot remove “boot kit” malware. This malwares removes boot-files and makes computer unbeatable and corrupt. Run “Windows Powershell”. It is an alternative command prompt for Windows. Type “ConfirmSecure boot UEFI” (without-quotes). If the result of command prompts comes to true, then it is confirmed that “secure boot” is working on computer.
3. Microsoft is encouraging hardware vendors to enable built-in security-booting for computers. It will lock out malicious “boot kit” codes which are developed with Linux computers. Microsoft is locks such hacked computers remotely and encouraging hardware developers to manufacture safe boot hardware to remove this dangerous root kit permanently.
4. Windows 8 supports, newly introduced technology namely, “supervisory mode execution prevention” Central processing unit (CPU). It initiates data execution and Prevention (DEP) in hard wares. It is better than software DEP and it creates safe CPU and stops buffering data overflow in order to prevent destruction of the hard-disc drive, RAM and CPUs.
5. In other versions of Windows 8, a good encryption mechanism known as “Bitlocker” is available. It is a new incarnation of software restriction policies. It is available with Windows 8 Pro versions. Windows 8 home edition users should download “enhanced mitigation execution toolkit” (EMET) of Microsoft. It is a free tool and a default option of it is very good.
6. Microsoft has improved “Sign-in” options for Microsoft Windows 8. Consider adding secondary log-in options of “change-pin” or “to create a picture-password”. That helps you to take password security practices to a top-notch security levels.
7. Windows 8’s picture password is an innovative way to preserve touch screen personal computers. When you hit the touch screen, combination of circles and gestures becomes part of your picture password.
8. Use “standard account” of Windows 8 for daily tasks and internet activities. It removes all traces of internet after restart. In this way, even if a malware is installed, it is removed after restart.
9. Use a router (hardware firewall) to restrict and manage network access. It is a hardware firewall and works better than a software firewall. Router works effectively with a broad band and semi broad band connection. It does not do anything under dial-up networks.
10. Change factory password of the router. Use a secure password which is long coupled with complex characters. Time to time checks for security and cumulative updates of the router to set up security patches.
11. Use a modern “WPA2 encryption” instead of “WEP” or “WPA” encryption of Wi Fi protected access.
12. Turn off “Universal Plug and Play” (UPnP) feature of the router and computer.
13. With Windows 8, move the cursor to the lower left side of the computer and “charm” menu will resurface, from “search menu” type “Update”. From “settings” go to “Windows Update”. Set it to “automatically install updates”. It continues to check newer updates within certain intervals to make PC secure.
14. Uninstall unnecessary software which will keep personal computer safe from “attack surface” hacking. This is another form of “buffer overflow” attack which will unnecessarily fill up RAM as well as a hard disc place to make slow or sluggish computer. Slowly, it slows down the central processing unit (CPU) of the computer and if this state prolongs in the long run it can damage hardware and break computer to a stand point.
15. Delete all instances of Java, QuickTime, RealPlayer, Yahoo Messenger, unnecessary web browsers and software. By critically injecting codes of “attack surface analyzer” inside malicious software, hackers hacked into PC and steal personal information. Most of times, in Windows, Microsoft provides many software which can cater your needs completely. It is better to use less third party software so that danger lurking out of “attack surface” hacking will be minimal.
16. “Enhanced Mitigation Experience Toolkit” (EMET) is a free security utility from Microsoft. It works best with the latest version of Windows (Windows 8 and Windows 8.1). It optimizes existing application configuration settings. It adds an extra layer of protection for Internet Explorer, Word Pad, Microsoft Office, Adobe Reader and Oracle Java. EMET adds rules of “certificate trust” for Microsof. It enables reporting through “Windows Event Log”, “Tray icon” and “early warning Program”. It is not an obstructive program and it does not disturb users with continuous flash messages.
17. It is always advisable to install the latest version of “Internet explorer”.
18. Enable “User Account Control”. It is from Microsoft and it is skillfully integrated with Windows and it rarely advent to screen to ask for permission. Its configurations are nice and in its default setting it works best.
19. UAC of Windows 8 creates a virtual file system, registry virtualization and protected mode to secure critical system setting from intruders.
20. Windows 8 has a new anti malware program known as “Windows Defender”. It is rebranding of “Microsoft Security Essentials”. It is now installed with Windows 8 as “Windows Defender” and it is a proactive security suite runs in background and windows update keep itself up-to-date. “Windows Defender” is now free for home users as well as for small businesses to use up to ten computers.
21. Apply safe computing practices by recognizing fake website versions of popular websites such as face book, twitter, E bay, paypal and do not click-through these websites. Do not provide personal information and identity in those faked version of popular websites. In this approach, you can alter every possible phishing attempts from hackers.
22. Back up your data regularly. Buy a good external hard drive and connect with Windows 8. It has built-in mechanisms to attest third party external hard drives. Turn on “File History”. It saves copies of your files so you can get them back if they are lost. It cans safe copying of files every hour in default setting. It is fast and does not consume huge system resources. It keeps offline cache to create a series of synchronization between computer and external hard drives. It creates an incremental backs up of the entire hard drive of the computer.
23. Windows 8 has dual schizophrenic graphic user interface (GUI). One is age old desktop and the other is infamous “metro style”. In “metro style” GUI, Internet Explorer 10 (IE 10) works with “enhanced protection mode” (EPM). EPM is a standard protection mode of a website in which all entry points of malicious attacks and hacking attempts are eliminated before the website loads into IE10.
24. Adobe reader is well known for leading portable documents. It is equally a honeymoon place for all attackers and for ages it has been continuously targeted by attackers to enter into persons computers. Windows 8 has a built-in security “PDF reader”. It runs in “metro style” GUI. It is always a better idea not to install “Adobe Reader” in “Windows 8”. One should use default “PDF reader” from Microsoft.
25. There are many ways to secure “Adobe PDF reader” and run it in “protected mode”. Javascript setting of “PDF reader” may be disabled to stop malicious-codes. First install the latest version of “Adobe PDF Reader” from Adobe's site. Then open “Adobe Reader” and then to “Edit”, then to “preference” and then “untick” JavaScript. This is a per user setting. Then configure “security, (enhanced) ” and override protected views to put additional limitations of “Adobe reader”. Protected mode is same as standard user account of Windows 8. By opening protected mode of “Adobe reader” in the standard account of Windows 8, you assure a perfect secure computer.
26. It is always a nice idea to go for “2 step verification” for Google products. Most of Windows users connect to the Internet and use a Google search or use Gmail and other Google services such as YouTube and Blogger.
27. Beware of shoulder surfing. Even a strong password from “biometrics” configuration can be hacked from persons who are watching you from behind.
28. Most we-browsers are almost secure. They get regular security updates. Browser add-ons are mostly dangerous for security of browsers.
29. Purchase computers from a well-known hardware vendor. Use a good firewall. Firewalls are like virtual police to enforce security inside environment of operating system.
30. You may be given to a full disc encryption (FDE) laptop. Your computer and data will be protected even if you have been defeated.
Importance of a written security policy in an enterprise:
A well-written security policy of an enterprise advises members to continue within certain specified parameters. It helps law enforcement agencies to investigate disciplinary standards and monitoring systems consistent with industry’s normal to detect and prevent various security violations. It requires authentication of users, authorization to grant privilege access, data privacy and data integration, non-repudiation, security of servers and evaluation of return on investment (ROI). Provisions for ensuring access to administrative control include the process of authentication, privilege access, automatically logs out of unattended computers and detecting of discrete connected computers inside the enterprise network. Strong password policies for all accounts to secure access control mechanisms of computers. With the widespread use of internet, you may want to restrict users from uploading and downloading of files. Stops support from anonymous file transfer protocol (FTP) and use of secure socket layers (SSL) all across the organization for data encryption. It stops users to exploit existing networks to send important files to different locations. In an enterprise network, paramount importance is network security. Most communications and sharing of information across networks are achieved through high speed internet. Importance of written security policies ensures implementation of robust security policies all across organizational networks. Here, are a few suggestions.
1. Configure firewall to permit pre-configured security websites.
2. Block non-authenticated Telnet logins and automatic ping queries.
3. Emphasize the need for strict access control and assign responsibility to staffs in bright cut directives.
4. Virtual Private Network (VPN) pass through solid encryption to remove information related with privacy and data integrity.
5. Every standalone computer networks must pass through appropriate authentication techniques.
6. Modems of corporate networks should not be connected directly with networks connected with workers. There should be a sharp line of separation between those two networks.
7. Ensure proper physical security to computers with proper security cables and locks to prevent stealing of computers.
8. Attach computer system alarm and close circuit camera inside server rooms.
9. Train employees to be aware of shoulder surfing. Train them to use long and secure passwords as well as never leave computer unlocked.
10. Place the server in an access-controlled room.
11. Isolate all network infrastructure systems which include routers and firewalls and implement genteel code of least privilege access to all units of enterprise network server.
12. Maintain audit trail logs files to scrutinize unauthorized activities.
13. Install software such as “Network Monitor” and “Intrusion detection system” (IDS) on the computer to enable a vigilant watch on network behavior and activities.
14. A proper contingency planning that includes quick time to reach normal functions after imminent disaster. A proper disaster recovery plans should be available to nullify the effects of server down time.
15. Vital e-commerce circulars and documents should be incrementally back up regularly to external hard drives. Those hard drives should be kept in a sheltered and isolated place other that place of these physical servers. Physical protection to back up server must be given in accordance with industry’s standards.
16. Test drive disaster recovery plans annually, and check its shortcomings and if found something negative updates critical vulnerabilities with security updates and critical policy decisions.
17. Strong disciplinary actions on fraudsters within staffs including suspension, termination of contracts or criminal prosecution of revoking public security policy documents.
18. Train and communicate each segment of security policy of your organization to staffs and implement good marketing methods to distribute security guidelines.
Scope of computer security policies:
Implementation of good security policy lead can safeguard strong financial losses, protect intellectual property rights. It enhances competitive advantages over immediate competitors. It helps to avoid unwanted litigation. Organization security policy is a dynamic document. It has to be keeping on evolving and changing according to changing time and circumstances. Therefore, it is imminent to reassess and revaluate security policies to counter new security threats arising from different strategic shifts of organization. Here are some suggestions about the scope of computer security policies.
1. Corporate security policies go through the process of security assessment, project consulting, implementation and future developer support.
2. Create robust guidelines for constructing password rules, devise session time out parameters, and construct a well-balanced security policy for implementation of organizational guidelines.
3. Access different risks involving denial of service (DoS) and security attacks on network computers.
4. Make log files for system outrages and malicious activities.
5. Establish duplicate servers at unknown places and back up entire copy of server to it.
6. Avoid fraudulent phishing mails which are intended to steal critical data of an organization.
7. Enable remote device protection for smart phones and tablets used for authorized purposes. All major mobile operating system has built-in applications to enable remote device control in case phone gets lost or stolen.
8. Scope of organizational security policy is extended to work space, business space, enterprise space, hosted security services and total space security.
9. Periodical inspection on access control, device control, application control, vulnerability scanning, web control and content filtering to create a proactive mode of security.
10. Cybercriminals use social networks to steal personal security information of users. Post minimum subjective information in social networking sites like twitter, Facebook, My Space or LinkedIn.
11. Do not befriend with strangers.
Conclusion:
Crime is the dark side of society. Criminals have adopted modern techniques, in the modern world to keep up with ever changing technology. Anybody, who uses the internet, is at risk of becoming a victim. Arm yourself with the best antivirus package; utilize a completely updated operating system, latest versions of web browsers, and third party applications from a reliable and trusted vendors. The internet is a safer place to live in as long as we are equipped with the right equipment to avoid being a casualty. Idea of computer security is concentrated on data security and physical protection of computers. It relates to prevention of hardware damage, information theft and disruption of service. Computer security focuses on preventions of denial of service (DOS) and prevention of cyber-attacks. DOS is a temporary disability of performance reduction of computers when major hard drives crash with permanent data loss. Despite heavy technical advancement, most computer systems are not full-proof. Security is fundamentally problematic concept. Securing a system has traditionally become a battle of wits. Abusers, hackers and other perpetrators can secretly monitor your computer. Effective security cannot secure you from flawed procedural controls.
How is cyber crime actually defined?:
A notorious hacker is seating in somewhere at the outskirts of Russia or China with a laptop in his couch. He is generating spam messages or cyber bullying in coordination among different experts all around the world in creating a virus. Cyberspace is a super highway in action. It consists of invisible criminals. Tracing of their geo-location is difficult to achieve. They are not ordinary criminals. They sit at separate continents with a computer and Internet connectivity. They indulge in the cyber-warfare.
Computers and the Internet are part and parcel of human life. It is conveniently linked with transactions and product merchandising with a high degree of accessibility, intractability. Cyber crime is an illegal and illicit activity carried out through computer with internet. Cyber criminals can hack your bank accounts, indulge in identity theft anytime. According to European and North American countries at the Budapest Convention on Cybercrime on July first, 2003, the definition of cyber crime is, “an illegal act where a computer or a computer network servers as the location, means, target or source of the act”.
The effects of cyber crime on society:
According to studies more than one cyber crime happens in every 12 seconds. It amounts to lose more the $500 million each year. Cyber criminals have the ability to break password security. Many a times, cyber criminals will give you the lure of giveaways and they will ask for your email password or bank account details for this free promotion. Nigerian email scam asks for credit card information detail of individuals. Criminals impersonate themselves to get confidential information from people. They indulge in cyber bullying, sexual harassment and cyber stalking.
In the latest incident, one educated and financially independent girl built relationships through face book. Slowly, she becomes closer to the guy on the face book and they married on a date. After one year, first wife of her husband reached at that place. In the second year of their marriage, police caught both of them red handed while drug smuggling. It is the case of how a social media is used for a cyber crime to trap a girl. He married to her despite his earlier marriage and then he indulges an innocent girl in drug trafficking and drug smuggling.
Many a times, cyber criminal used to enter into computer others to steal important information about bank account details and other essential documents. They attack your computer by sending spyware, which could be staying inside your computer without your prior knowledge. The aim of this spyware is to steal information from your computer. It does not harm your computer. Bandwidth theft is other forms of gaining access to your internet connectivity. Yours broadband connection becomes a dial up connection. They will steal your internet time with these dial-wares and huge internet bill is incurred.

Cyber crime is easy:
Cyber crime is profitable. It is easy. Layman can perform this. Last year one cyber criminal who is illiterate in computer languages, sends virus inside a porn photograph. It has millions of download and it affects many computers all over the world. For the next six month cyber security experts have tough time to detect the areas from where it all started.
There are many regions in the world such as far off areas of Russia, Ukraine and China, which are a safe haven for hackers and cyber criminals. They are protected by some governments. It is also not clear, but an established truth that hackers paid percentages to these government agencies. In turn, these agencies never allow cyber security experts from other regions to catch and interrogate them.
Two years be one Chinese company produced an efficient anti spyware known as “Advance Security Care” and it became an instant hit. It has brilliant detection rate with zero false positives. Existing shareware biggies such as “Super Antispyware”, “Hitman Pro” and “Malware bytes anti-malware” are worried.
Virtual world and cyber crime:
At last, it proves that “Advance System Care” stole definitions updates of “Malware bytes anti-malware” thorough reverse re engineering processes. Due to the virtual world and anonymous use, the identity of the hacker and proof of its wrong doings is difficult to prove. Governmental and financial institutions are the most common target for cyber-crimes.
These Chinese hackers perform cyber attack anonymously, and then try to take control of a remote computer by gaining administrative privileges. Then, Government of India decided to have stand alone computer where significant confidential information is stored. Cyber hackers are dependent on Internet connection. A standalone computer is devoid of such internet connectivity.
Data diddling:
In 1996, Council of Europe, Canada, Japan and the United States drafted a treaty on cyber crime. In 2001, International Convention of Cybercrime, in Budapest signed by 30 countries. It gives cyber security experts the surveillance powers and permits them to store the intercepted data for advance investigation. Buy a good antivirus suit, keep your operating system and web browser up to date. Avoid cyber cafes for online purchases. Purchase it at home. Utilize standard accounts instead of an "administrative account".
Viruses are creations of bad software developers. Viruses are harmless still it is executed. After execution, it attacks the central processing unit and RAM of the computer. CPU usages become on the higher side and RAM becomes full. Computers become non responsive. It slows down your computer either through a central processing unit or through excessive use of RAM. “Resource Monitor” can showcase which process is eating vital system resources.
“System Volume Information” can show which software (here virus) is utilizing plenty of disc resources. These two tools are in Windows Vistas and later versions of Windows. It helps the common user to find out boggy resource eating processes.
It is easy to stop viruses. Install a suitable on-access (always on and runs in the background) anti-malware on your computer. It will check every process and network connectivity in order to keep your computer safe. It will connect to the Internet to download the latest updated definition. It is important keep your computer abreast with latest developments all around the world.
In addition to this, most modern anti-malware (antivirus+ anti spyware+ firewall) utilize cloud computing by connecting with their servers in order to minimize virus attack time. Virus attack time is considered as the time to create updated definitions to counter virus.
Threats against your online presence:
For this, most companies are now giving two types of definitions updates. One is the customary form of definitions updates through the Internet and the other is a vertical connections of your computer with antivirus company’s server and they control your computer and disinfect it before proper definition files are circulated. A virus cannot cause havoc inside your computer until it gains access to administrative-rights.
Windows 8 is the latest incarnation of Microsoft Windows. It has two set of accounts. One is the administrative user account and the other is a standard user account. Microsoft is encouraging users to use standard user account. A "standard user account" with Windows 8 is of two types. One is local and the other is Microsoft. In local you login to your user account and in Microsoft standard user account Hotmail account is merged with a limited account.
According to Microsoft, “A universal user account lets a person use most of the capabilities of the computer, but permission from an administrator is required if you want to make changes that affect other users or the security of the computer.
When you use a standard account, you can use most programs that are installed on the computer, but you can't install or uninstall software and hardware, delete files that are required for the computer to work, or change settings on the computer that affect other users. If you're using a standard account, some programs might require you to provide an administrator password before you can perform certain tasks.”
Standard user account:
With Microsoft standard account, all your information is synchronized with Microsoft Windows server. In a way, Microsoft will keep a strict watch on intruders. It has some privacy concerns. If you do not want this, it is better to go for a standard user account. Here, you can do every possible task and actions but you will have to give administrative-privilege to change critical system settings. In a standard user account virus cannot alter system settings. With a restart all the virus and nasty ware downloaded from the Internet will erase. In a way, Windows 8 gives optimum security to the ordinary user. Stay away from cracked software. Always download software from official sites. Do not use pirated software. Cyber hackers inject viruses in cracked software and distribute through Google hangouts or Samsung Chat on.
Internet gateway is web-browser. You connect internet through a web browser. It also downloads possible much groupware and Trojans. It is always appreciable to utilize a superior web browser. It is always nice to have a decent alternative browser such Opera, Google chrome or Mozilla Firefox. Internet Explorer 10 of Windows 8 and Internet Explorer 11 of Windows 8.1, is good and user can use it. Previous versions of Internet Explore have critical vulnerabilities which are numerous days left un-patched. It exposes users to viruses. Countless users force on-demand anti-malware instead of on-access anti-malware. It is not a good idea. User cannot manually monitor all the virus activities while with computer. It is always useful to have on-access always on anti-malware with regularly updated definitions files.
Denial of service attack:
Denial of service (DoS attack) happens through Internet. Various connections are open simultaneously from a computer to the Internet server so that the computer becomes slow and weird. Array of simultaneous connections to single server amounts to huge resources allocation, and ultimately crosses the maximum CPU thread, which causes the system to crash. Within seconds, your system as well as hard discs is bombarded with denial of service attacks to make a BSOD (blue screen of death) to your computer. It is a cyber crime. A clever hacker does not leave any trace of identity.
An old adage says keep your friends close, and enemies even closer. Analytical communications mediums such as local-servers, cloud the data base, LAN and web servers should not be open to public. Data mining restriction is a must for safety and security of organizational data structures. Decision support system (DSS) and enterprise resource planning (ERP) should be properly administered and all the safety parameters must be implemented. While working with a governmental organization at the beginning of my professional career, I was posted there as a computer administrator to oversee the daily activities. During those times for the first time computerization in the entire organization started.
What is worse is that most of the older employees who are proficient in manual works are feeling the pressure. Organization neither introduces the staff training program for executive nor any seminar as such. Executives are unable to cope with pressure. Most of them have neither had basic knowledge of introduction to computers. Yet, they have to work with computers instead of manual ledgers. This is why, acute vulnerability of data theft is surfacing as the majority of executives who are dealing with a user name and passwords, many a time, left computer open unintentionally. These are loopholes of organizations, which needs to be patched at the earliest.
Your personal data is worth money:
Due to large scale computerization inside of monetary organization, numerous customers are accessing their bank accounts with net banking. Financial organization always warns you about not to give passwords to strangers. Passwords are confidential, even the concerned organization will never ask it of you. Yours passwords transaction with the server is done through encryption.
After my graduation, I sent my curriculum vitae to diverse job portals. In the morning, when I checked my inbox with a smart phone, came to know a job offer from Maruti Suzuki. I eagerly opened it, but from the sender menu the sender name is not from Maruti, and it built the suspicion. Inside of letter, it was written you were selected for the post of a hardware engineer and for this you had to send 15,000 rupees as processing fee. I was amused with it as I knew, most of my class fellows, received company related conveniences to join. This was an example of internet fraud where the cyber crime will receive 10,000 rupees and then would become silent. I contacted GM recruitment of Maruti and he confirmed me that it was a fraudulent mail.
The Internet is a vast unregulated field. It is a savage world as distinguished political philosopher Locke once puts his ethical theory. One should always see and observe each data stream. Apposite Internet knowledge is the need of the hour. Remember nothing comes out for free. If any such freebies are in offer, then suspect it and investigate it. The case of fraudulent email of appointment as I have mentioned above testifies this.

Pharming:
Pharming is a virtual attack, which aims to transfer visitors of your website to another bogus website. Due to pharming webmasters observes sudden astronomical vertical drop of visitors. If you have ad sense approved account on your website. Visitors loss could directly reduce your income. Loss of visitors means the loss of popularity of your website. On the long run page rank of website comes down. It is always hard to detect the source of pharming. Pharming attack is commanded through DNS server. It is not traceable and most of their runs with lagging time. Even if someone detects the source, still it is difficult to trace the persons as most DNS servers run several hours late. DNS servers modify your host files. By using standard accounts or reduced privileged account on your operating system, pharming attack can be avoided. Remote server control on your host file would require administrative privileges.
Internet Explorer 10, is the most secure browser at all. Try to use ad blocking software on your computer as this does not allow bogus pharming as they have pre-configured list and which is updated regularly.
Threats against your online presence:
One day as usual when you enter user name and password, to your Gmail account, Gmail is retuning with this saying password is wrong. This means that your password is changed and a Gmail account is hacked. Facebook is popular worldwide. It is a social-media networking, where the user put all pertinent information, updates and other forms of data sharing. Facebook is famous for its application and games. One should always be careful while permitting applications. Fraudulent apps can steal your data and then share your private information outside. It can store your information, profile information, data and timeline information so as of information of your friends on a remote server.
It poses a serious threat to you and also your friends. It is always a good idea to investigate about the publisher of apps, and then install it within your face book environment. While granting permission to apps through “O Auth” it is always advisable to go through entire details of apps. Twitter is a social media networking sites to post small messages, pictures and videos. There are plenty of third party apps which can run through twitter as a client if the user permits it. Before installing any such apps to twitter, find out the source and author information. It is always a good idea to permit and install apps from reputed firms.
Face book is meant for friends not stalkers:
“Yahoo Messenger” is an open platform and here everyone can connect with the other, and the privacy-setting of it is very minimal and everyone can see the other if they both are online. In this way, the vitality of this once powerful and popular messenger vanished from the scene suddenly. It is replaced by Facebook with powerful privacy-functions, but yet many users do not know it. For this they fall prey to fraudulent persons who are browsing here and there. Innocent girls should be properly educated t who have a strong social presence and can avert such anonymous users. They can block them straight forward and can ban them from seeing their profiles. Facebook is meant for a friend not stalkers.
Ever since Tim Berners Lee invented the Web, various web related applications such as Blogger, face book, twitter and so on gained its prominence.
Owing to these streams of data flows across the Internet like never before. Data are essential and it gives money. There are people who want to lurk in to your face book and twitter account to know your favorite past times and after knowing this they tend to sell it to advertisers for promotions. Five years back, I registered my details and curriculum vitae to job portals. Though after some days only spam emails reached to me, and also I have seen increase of spam messages in my inbox. It does relate to me that probably somewhere at some of these portal have to sell my email to advertisers. It is better to log in to Gmail with a standard user account and send all those messages to spam folder. From there send these messages to spam and unsubscribe from them. Before opening any message, from the top observe the sender information to confirm mail as original and secure.
Please beware of fraudster:
Facebook fraudster can gain access to your account. Data will be downloaded with the zip format and then they will open a new account and upload your data and will say the singular account is hacked and fraudulent account which they open is the original account. In this way entire shifting of yours face book identity is done and all the friends of your account could be intimated by fraudster to connect with them with the original account. In this way he can now control your account and offend your friend with ease.
This is why; one should not share all the information at all. It is always, a good idea, to have to restrict your sharing options so that others will not gain access to your information. There are some who try to build a number of friends and try to add countless friends from countless sources, without identity. Facebook is meant for real friends who are also in the virtual world. A friendly request from unknown sources should be rejected out rightly. It is always desirable to ignore such requests as at any point of time you might wonder unknowingly sharing some vital details of life streams of your friends. So, please beware.
Don’t break laws unknowingly:
The Constitution of India has given citizens of this vast country the right to freedom of speech. On the other hand, there are certain responsibilities attached with this. One has to be extremely cautious while posting something to Facebook timeline or to twitter stream. One should not feel that no one is watching. One should always be careful while dealing with these posts. On the latest, President of France showed his apprehensions about the classified service of US spying against him. President of US Barack Obama has ordered an investigation. So, it is the duty and responsibility of the people who posts to see and watch all the information being posted on his behalf. Some additional person would never ever be able to remind you of this. Previous years how two girls from face book have been arrested for their comments on Face Book?
In the real world, it is always said that thinks before you talk. In the simulated world, it is said think before you post. Suppose you have constructed a group within face book and begin sending the links of pirated software to users. Unknowingly, you are doing a terrific loss to Software Company and for this you are breaking the laws. It is the same as when in of the line you are trying to sell pirated software DVDs. It is different from giving information to users the information about giveaways, software updates and other forms of deals and coupons. Remember everything what we move online such as blogging, forum posting, twitter status updates are being logged in somewhere in some computer which is acting as a server. Every action performed is being documented and thus gives the perfect proof.
What is the remedy?
In a lonely space, look at the mirror and then ask yourself, when you are offline, what are the works which will not be entangled you with legal actions. The same does apply to online world. One should not write anything that would hurt any people as well as any people. Do not get involved yourself with controversial topics as well as confidential information. Do not get inspiration from people who believe profanity is the order of the day. Always behave with respect and do not involve in harsh talking with anybody. If that situation happens, it is better to move away from these discussions. If this continues for some time, it is better to block that person from the list of friends and also there are some additional settings through whom you can entirely block that person from accessing your account.
Do not use slang and harsh words. At present, we are living in an internet world where there is no such importance attached to this. With due course of time, all these will be difficult to pass it on as for that time you should start to regulate yourself properly. With Internet, you send text to person. Emotions cannot be attached with these texts. You should write in a style in which the proper circulation of emotional attachment to the talk which you put in the text should be done. One should always write in standard English instead of using slang words. Treat your online mates with respect. You will never know how your friends would react to this. It is better to behave properly in order to stay away from legal discourse.
Just be social not an addict to it:
While at the office do underestimate with and trust of colleagues. Some time back you may have negative posts about your boss and shared with your trusted friends and after some time, you should have removed from those or change the privacy setting. If these posts are shared to your boss, then it can spill into trouble. It is better to stay out from inflammatory posts. Another difficult feature of social media networking is “share” feature. When you make a public post, Google+ users can share that post and this expands the audience level and reaching the level of the post to wider masses. In twitter, “Retweet” is the share feature and through this your short post is being shared to wider.
Parental guidance:
Social media is reliable, and do not be addicted to it and if so, then you are becoming a patient in it. Mortality is strong emotionally as well as mentally and when the simulated world is trying hard to entangle in its superfluous environment. Humanity will be bound to make mistakes from it. Personally, I use it to share my writings into a social-media networks. Lack of inter personal interactions is the conspicuous part of social-media and with it comes the gap of reality. Everyone who is using social networks should learn this and try to implement this in real terms.
If you are falling into the trap of social networks, then it is time to go on vacation. Sometimes, social-media networks can give a finer level of depression from variety reasons. One such case occurred here in my native city, when one of my cousins who are jobless has recently joined face-book. After joining plenty of his old class fellows added him to friend list. He saw their profile and realizes that most of them are as respectable jobs and he considers himself to be a failed person amidst these jungles of information and became sad.
Social media networks are not true and every detail data reveals here is not true. One has to verify it and one should not be so intense about it when entering into this. These incidents do not directly reflect the division of cyber laws; it does make depression and schizophrenia. Such state of mind can make situations for people suffering to translate into actions in a harmful way. It is immoral for individual as well as family concerned.
Do not just upload any pictures randomly:
Do not just upload any pictures randomly. Do not take pictures randomly and also do not flash cameras where photography is prohibited. Terrorists can gain this as advantageous and will try to inflict a curse through their destructive activities. After some time, there are heavy possibilities of catching them by security agencies, and when they will reveal the source of their information, that can spell trouble for you, even if you are innocent and ignorant of such advances. There are numerous photos sharing websites such as Flickr, Picasa, Google+ photos, twitter and Facebook. One should always be vigilant about uploaded contents of information.
While sharing images online one should always be conscious about copyright infringements. Before sharing any image, it is a well known fact that, these pictures are copyright materials of some other people. It is against the law to share images taken by others without their permissions. Always use your common sense while sharing other’s pictures. Two things need to be considered here. One is too aware of copyright of these pictures and the other is as well aware of whether these pictures are of forbidden areas are not.
Avoid hate groups:
The Internet is an uncontrolled territory. It is a dashboard of all goods and evils. Everything spreads fast here. There is little chance of controlling and policing. Due to the advent of Web 3.0, users are now connecting multiple accounts through “OAuth” and information spreads fast. Twitter is faster than earthquake. News can spread within seconds far and wide. There are many forums and interactive groups where you can find the maximum number of hatred messages to promote opposite popular views. Many a times, some members across the line and that is against the laws. Do not try to enter into such groups as these can pose you serious problems legally and emotionally.
You will never know when any hot topic can stretch you to emotionally hatred messages. Internet can be misleading at times, and it is important to observe the trends and also before condemning and claiming it false be sure you have sufficient claims of truth so that later on when you are challenged before court of law, you can create yours defense within those claims. While discussing any such debated topic within the sphere of a forum, it is absolutely essential for you to stay away from blind criticism. Healthy criticism is welcome in society.
It is always suggested thinking before you write and always consider everything in terms of legitimate point of view. Be aware of fake accounts. There will be some accounts which are there to impersonate someone. These are phony accounts but run by some anonymous people. In order to know the actual account, twitter, Google+ introduced the concept of verified accounts. In this approach, if someone wants to connect with definite individual then he should have checked his profile for authenticity.
The broad definitions of cyber terrorism:
Slowly, we have been pretty reliant on the Internet for our day to day activities. What if at a time, when some of the indispensable services come to a halt due to some reason. Here is one such practical example. Phailin hurricane struck in my city on 12 th of October 2013. It is fast and furious and with it comes the destruction of essential services. Continuous power failure for 50 hours occurred in and around the city. Inverter goes out within six to eight hours. Mobile and smart phones drained out batteries within ten to 12 hours. Mobile networks go out of control. There is hardly any medium of communication left. It does feel as if one is staying in the dark ages.
This gives a sense in extra ordinary situations. Mobile networks go off. Nonetheless, what if, due to hackers most of mobile networks go off, and people are still searching for towers in order to connect with others. What if the traffic control system of the city goes down? In action movie Dhoom, the fraudster John Abraham, defuses the traffic system in order to move quickly after stealing. We are too much dependent on the computational system on our day to day activities. So, when something attacks the system and the system goes offline, everything dependent on the system goes out-of-order.
How shameless can cyber-terrorism really be?:
No system is perfectly safe and we have to learn to live with it. There are sundry scientific fictional movies which depict about, how the fight between good and evil can happen in computational domains. The system depends upon numerous factors such as unique operating systems, servers and other protocols. When one such series of systems comes to halt, it reflects upon the entire architecture and the entire servers come to a solemn halt. Hackers only have to target one specific node of entire computation architecture in order to halt the entire system from running. Movie “Lice Free or Die Hard” is one of the best examples of how cyber terrorisms work in real time.
Diagnostic systems are controlled by highly skilled and trained professionals. A team of hackers has really tough time in cracking those systems. It is time which matters the most. There are times, when every system shows loop holes and experts are trying to implement diagnostic patches in order to save the system from external vulnerabilities. The possible exploitation of these critical vulnerabilities by hackers can make a complete disastrous situation for the company. Further, antivirus companies are working hard to stop these hackers.
Safety tips for end users in IT dealings:
Ours life has been revolving around the Internet. Many a time, we tend to over reliant on the Internet for our day to day activities. Now, instead of going to shop at the mall we are searching for the best values offer websites such as naptol or flipkart in order to receive materials at home from door to door delivery. Many a time is scheduled for electronic wallet payment system we have to pay through our debit or credit card to these electronic commerce websites. With modern cyber crimes such as phishing and data theft on the rise, it is better safe than sorry.
Protection of personal and private data is important. Google has pioneered the movement of people to come out of anonymity. It’s all in one Google+ account which needs your proper identity. But Google is trying hard to remove the barriers of anonymous which are against the ethics of the Internet. Cyber crime occurs when an ignorant person is the Internet. While during graduation, I used to reach a cyber café where I would like to check my in boxes. If someone wants to hack that email, then the original owner would not be able to access it at anytime.
Prevention is better than cure:
Apposite Internet education is the need of the hours. Hackers rely on their coding expertise, but they also used to watch internet behaviors and work accordingly whenever they get any such opportunity as mentioned in the above example. It is always better to have a dedicated firewall installed on your system. With Windows 8, with the advent of the parental control system, it gets major system revocations. One can use it in order to have a perfect child lock on accounts. Watch your children activities. Sure, your children do not meet online friends in off line locations. These virtual friends are fraud and meant to cheat your children.
If such a meeting happens, then choose a public place, for the get together in front of adults. Adults have seen life and will able to differentiate fraudsters from original humbles. Cyber languages are imperfect, and ask your child to refrain from using those in public life. Advise your child not to upload a photograph to cyber friends. Always use Wi-Fi connectivity inside your home. You can keep a vigilant eye on your child’s Internet activity. Advise your children not to enter into any such websites or services which charges money. Unknowingly they will enter into these sites incurring heavy expenses to your wallet.
While at Internet always be careful and mindful what you are doing there. Never writes down your password on any note pad apps. Memorize your password. Be wary of shoulder surfing. While writing password, always watch both sides of your shoulder to see whether anyone is there staring at your password or not. People used to turn off “auto update” feature of computer. They used to do this in order to save vital bandwidth prices. They are doing it wrong.
Intrusion defense system (IDS):
Hackers are waiting for unmatched computer with lack of “day light saving time” in order to find the loopholes inside your computer. It is always advisable to patch critical vulnerabilities of computer whenever it is necessary. It is important to have a standard form of security. If you have too much security, it will frustrate the user. In the initial stage of development of Comodo firewall, introduces to intrusion prevention system (IPS) which is a stronger form of defense against malware attacks. User used to confront with so many questions of allowing or disallowing different processes. This is ultimately creating a sense of paranoid about security.
Users feel no security is better than too much security. This is not. No security is complete submission of your computer to hackers and intruders. Most computers can be easily configured to have maximum security without implementing intrusion defense system (IDS) mechanisms. Yours firewall is the gateway to Internet. Use a good firewall if you are using older Windows operating systems (OS). If you are using the latest incarnation of Windows, then it is better to use default Windows Firewall. It is one of the best in business. It works silently securing your system. According to Microsoft, “Windows 8 firewall helps prevent hackers and malicious software from gaining access to your PC through the Internet or a network”.
Change with time:
With the advent of modern computing, hackers are also enhancing their basic intelligent practices. Before connecting to internet, update your web browser. Most email providers have a built-in tool to report, suspicious emails to their server. Credit cards are a major source of fraud. Most credit cards are attached with your bank account. Keep your card details and CVV confidential. While swiping cards at the store, wait till the pecuniary transaction is over. If you receive unsolicited calls to request for your account number, never give it. Then, call back to your credit card service provider to check back. Never ever any such pecuniary organization would like to take back your passwords and account details. Beware of such phone calls and never influenced with it.
Identity fraud:
It is better to avoid these as they can access your personal information and then sell it to divide marketing ventures. Hackers will try to impersonate your account and steal your identity from yours. It is better to sign in with “Google alert” with your name, and Google will report it to your primary inbox whenever your name surface anywhere in the web. Online shopping is convenient and you can shop while staying at home. Never, links your primary savings account with your credit card.
Most hackers turned on yours “Forgot Password link” in order to break your password. Create your own question and answer in order to have a secure password. Public computers use cookies, user names and passwords, in order to revive your sensitive information. Use virtual keyboard while signing into an online bank account. Use a “Virtual Credit Card” (VCC). This feature is available to net-banking users.
Conclusion:
The internet is a superb device; it is part of our life. It is not a holy cow. There is a dark side of the Internet. It is the cyber crime. Sadly, it is on the rise. Employ proactive defense to defend your computer from sudden cyber attacks from any online transactions. Employ preventive measures. Laws on cyber crime are quite complex. It is not easy to limit those laws in a particular field. Cyber crimes are ever changing phenomena. Laws related to cyber crime should be changed accordingly. According to Alfred Pennyworth (The Dark Knight), “Some men just want to watch the world burn”. Cyber crime has been performed in the past and it will be bigger in the days to come. Happy reading and stay safe.
More Articles …
Page 1 of 24