Now,the question that arises is, HOW IS IT DONE? Let me explain.
There are 2 types of compression:
1. Lossless Compresssion: In lossless compression,as the nae suggests,there is no loss i.e. the data is fully recovered on decompression. Eg. winRAR files,WinZip files.2. Lossy Compresion: In lossy compression,there is a loss in the data while compression i.e. thecompressed file is never exactly equal to the original file. But, the loss is generally not noticable.Eg. MP3 files, JPEG pictures.
How does Lossless compression work?
The answer is just one word "redundancy" i.e. repetition of the same data again and again.
Let us consider an example:
"Democracy is government of the people,by the people,for te people".
If we consider a charater to occupy 2 bytes in the memory,then the sentence occupes 138 bytes. You might notice that the words "the" and "people" are reapeated 3 times. So, we create a dictionary by assigning a number to these words. Now we can use the numbers in place of these words. So the sentence becomes:
"democracy is government of 1 2, by 1 2,for 1 2."
The dictionary contains:---1: "the" , 2: "people" .
Now,the sentence along with the dictionary occupies only 124 bytes. But, the compression program doesn't see this sentence as a group of words.It sees this as a collection of characters.So, its doesn't see which words are repeated. Instead,it sees which combination of charascters are repeated. So, it may take " the people" as a single unit. So ,the dictionary may contain "1 : the people".
Now the sentence becomes :
"Democracy is government of 1, by 1, for 1".
Now, the sentence along with the dictionary occupies only 104 bytes.Thus, we have achieved about 25% compression.And this is just one sentence! Imagine the compression in an entire article,chapter or even the entire book!.
The compression is much more in the programs written in programming languages like C++,java,visual basic,etc. where some keywords are repeated again and again. This was the simplest compression algorithm. There are many others like HoffMann coding and LZW algorithm.
Now,if you are really interested ,try compression this sentence:
"Ask not what your country can do for you,ask what you can do for your country".
This was about lossless compression.
Lossy compession works by removing informatin in such a way that it isn't noticeable. I may write about itnext time.
Just for information ,this article's size is 2842 bytes in .txt format and 1,143 bytes in .rar format(60% compression).
--Atul Barapatre
Java Developer Kit
It is a collection of tools and necessary documents for making Java applications and applets.
The JDK consists of :
1.the Java compiler javac.exe to convert Java program into bytecodes.
2.the Java interpreter java.exe to translate bytecodes into program action to be executed by the JVM.
3.the Java debugger jdb.exe to death Java programs.
4.the Java disassembler javap.exe to display certain specific interfaces.
5.the Java header file generator javah.exe.
6.the Java documentation javaDoc.exe.
7.applet viewer
I have noticed that many persons do not have the proper idea of what is done usually in software or IT companies. Even some of the students studying Information Technology also have doubts about it. To clarify the entire thing we need a brief discussion about this.
Most of the software companies do not involve themselves in creating public software like Photoshop, browsers, media players etc. They involve themselves in making software for industrial use, e.g. Hotel Automation Software, Library Management Software, Banking software etc. Their work is contract based. When a company (such as a hotel) wants to automate their work, they contacts a software company and tells them about their requirements. In this step the software analyst interviews the customer about their requirements and then removes all kinds of redundancies omissions and inconsistencies in that requirements. After all these have been done the entire thing is written in a document called SRS document.
Next, software building is started according to this document and after the entire software is built, the software is tested to check if it is working or not. After the customers approval the software product is sent to the customer.
Though the software building is complete, one phase continues for a long time - it is the longest phase of software development, called the maintenance. It concerns with improvement, error correction etc.
Thus in case of software engineering, no actual or physical product but a virtual product is built.
Software development life cycle or SDLC is a collection of well defined ordered steps which a software designer follows to build the software. These steps are called development phase. The steps used in SDLC are as follows:
1.) Feasibility Study, 2.) Requirement Analysis and Specification 3.)System Analysis and Design 4.)Coding and Unit Testing 5.)Integration and System Testing 6.)Maintenance.
1.) Feasibility Study: In this phase it is checked if it is technically and economically possible or not to build the software.
2.) Requirement Analysis and Specification: In this phase the system analyst interviews the customers to know the requirements and then write down the requirements in SRS document.
3.) System Analysis and Design: In this phase the requirements are analysed and converted to a form which can be easily transformed to source codes in any standard programming language.
4.) Coding and Unit Testing : Here the each modules of the system design is converted to source codes and each module is tested separately.
5.) Integration and System testing: Each module is added one by one and the partial system is tested.
6.) Maintenance: This is the longest phase in SDLC. Maintenance includes error correction, performance boosting, adaptive maintenance etc.
Internet A Growing Need of our Nation, Internet is best option to learn, enjoy, and even earn from it. Internet help students in their studies, a mother in learning cooking, a kid to play games, a man to do official work. In today's arena it is even used for chatting with friends, relatives who live hundreds of kilometers away from us. There has been a steady growth in Social Networking Sites like Facebook, Skype and many more.
But using internet is not so safe, it can even take us on road and can make us a beggar in a minute! Children using Facebook know only how to chat but they don't know who is behind the ID. There are many Black Hat Hackers - ( Hackers who hack for Illegal Purposes). They create fake ID's that look exactly as a victim's friend or relative and extract confidential information from the victim. There is one another method known as Phishing which is the latest way of hacking.
Phishing is a technique in which hackers create a log in page which exactly looks like the official page of Website and they send it to victim and when victim clicks on it they are redirected to " Sign In " page and when they enter the information it directly goes to the hacker and they get hacked!
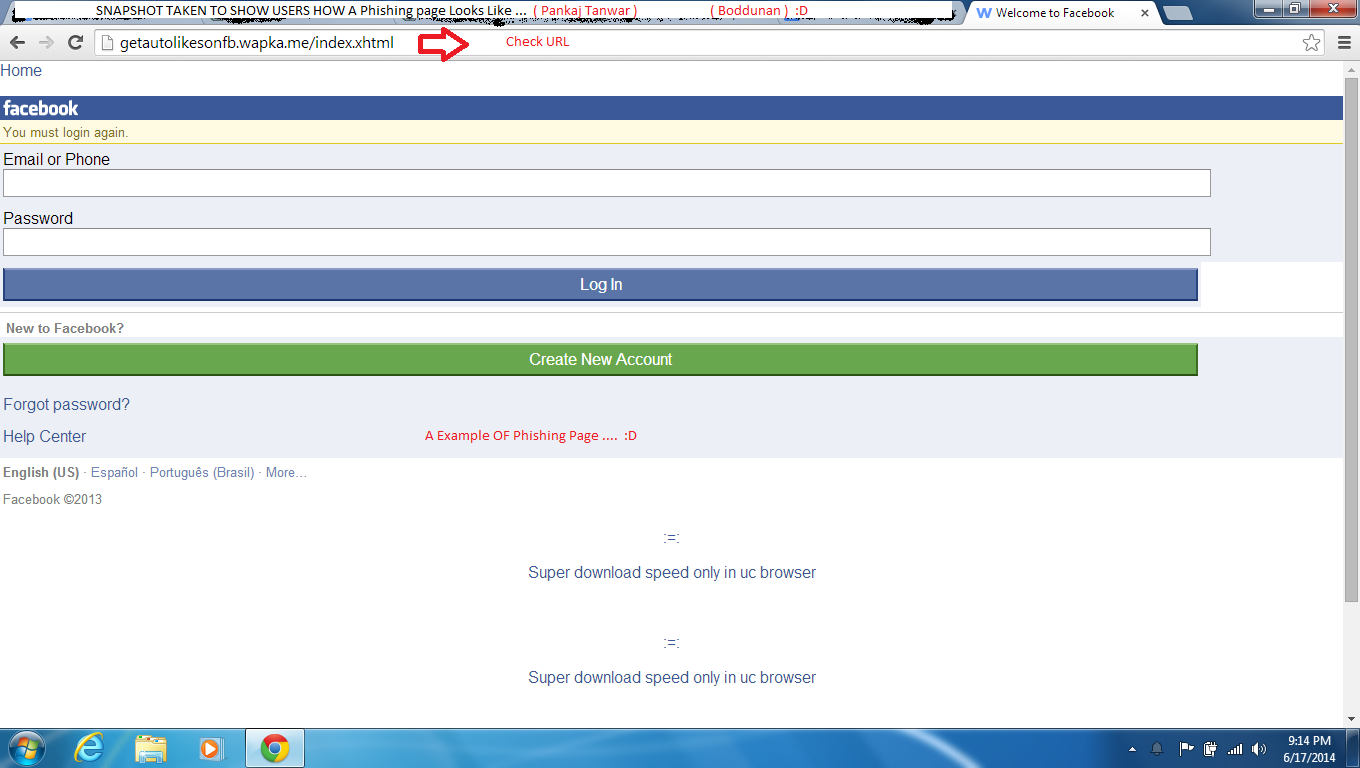
Steps To Be Saved From Phishing Attack :-
1. Always Check The URL of Website you are visiting .
2. Never Click on the Shortened URL ( Like Adfly ) . First Check it then click on it .
3. Never give your confidential information online to anyone .
4 . When You See a Log in Page which asks for your Email ID and Password , always check it's URL from address bar. ( Sometime Phishing page are created just by changing a letter on Main Website . ( Like www. Facedook .com )
5. Always have a Antivirus installed which checks the web pages whether they are secure or not .
Internet is a great tool to learn and explore , but use it in a safe way otherwise you will have to pay for it . This Phishing page can be created of any website ( Not only Facebook ) . It can be created even of Bank Websites and with it a Hacker can transfer all your savings to his account within a second . So Whenever You Come to this type of page - Be Aware and Report it to Cyber Security .
It is Illegal to Hack but if you write your information with your own hands - It will be your Mistake !
Be Safe BE Alert .... !!
More Articles …
Subcategories
Web Hosting
Web Hosting is a service offered by web hosting providers to the individuals and organizations to make their websites accessible on the internet. Depending on the requirement, one can avail different types of web hosting such as shared hosting, dedicated hosting, virtual private hosting, cloud hosting etc.
Page 95 of 193